
The Directory API represents a powerful extension of SGNL’s Access Service suite, designed to address complex organizational data requirements that go beyond simple authorization decisions. While the other Access APIs answer questions about permissions and access, the Directory API answers a more nuanced question:
For this Principal performing this Action on this Asset - tell me about this Principal
The Directory API enables organizations to expose and return complex structures of the SGNL graph while maintaining the hierarchical relationships between entities. This makes it particularly valuable for organizations with custom entitlement stores, complex role hierarchies, or intricate node relationships that need to be preserved in API responses.
The Directory API maintains the structure of SGNL’s graph directory when returning responses, enabling organizations to:
To get started with a new Directory:
nodeName will be the key name in the json response that includes that object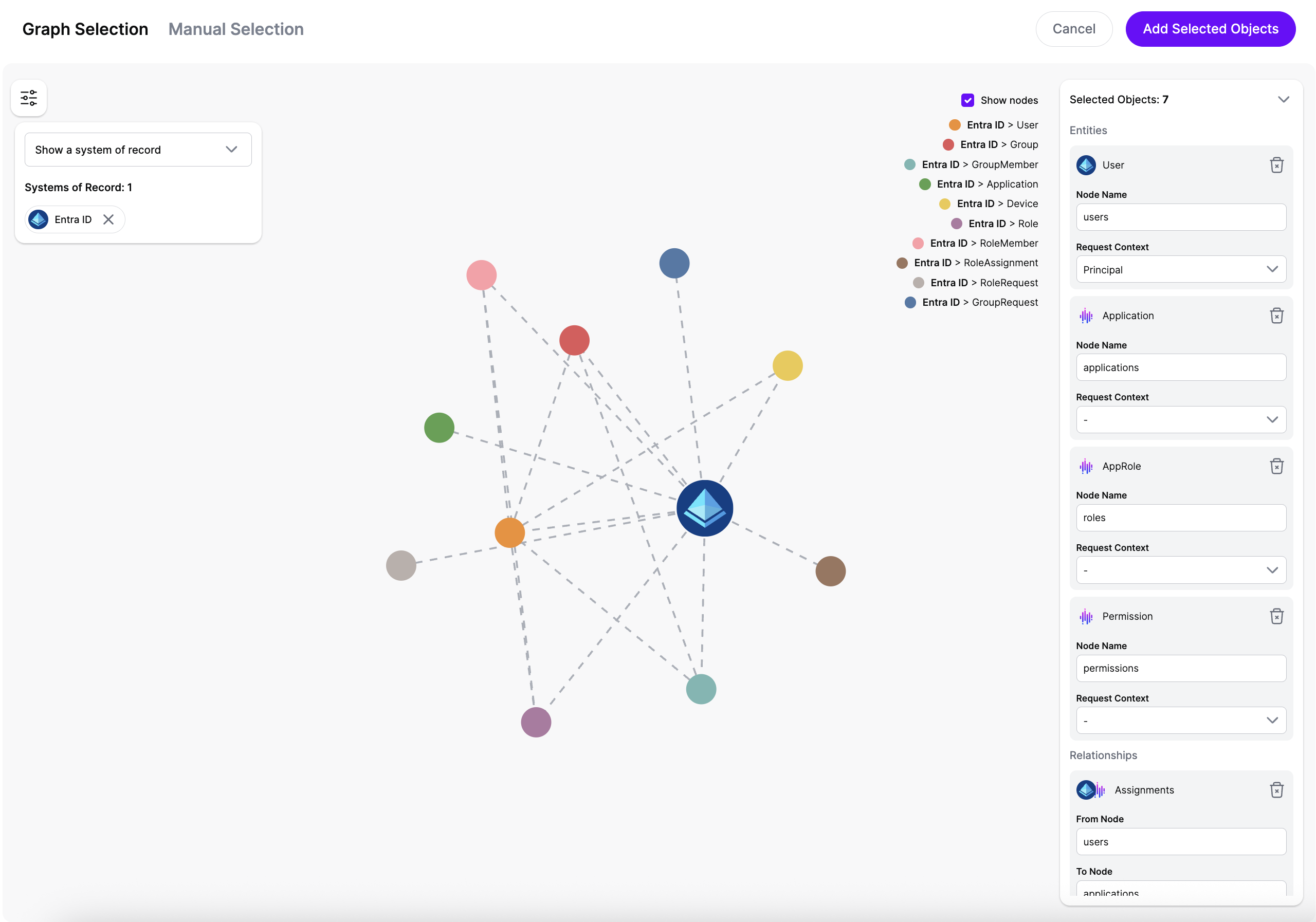
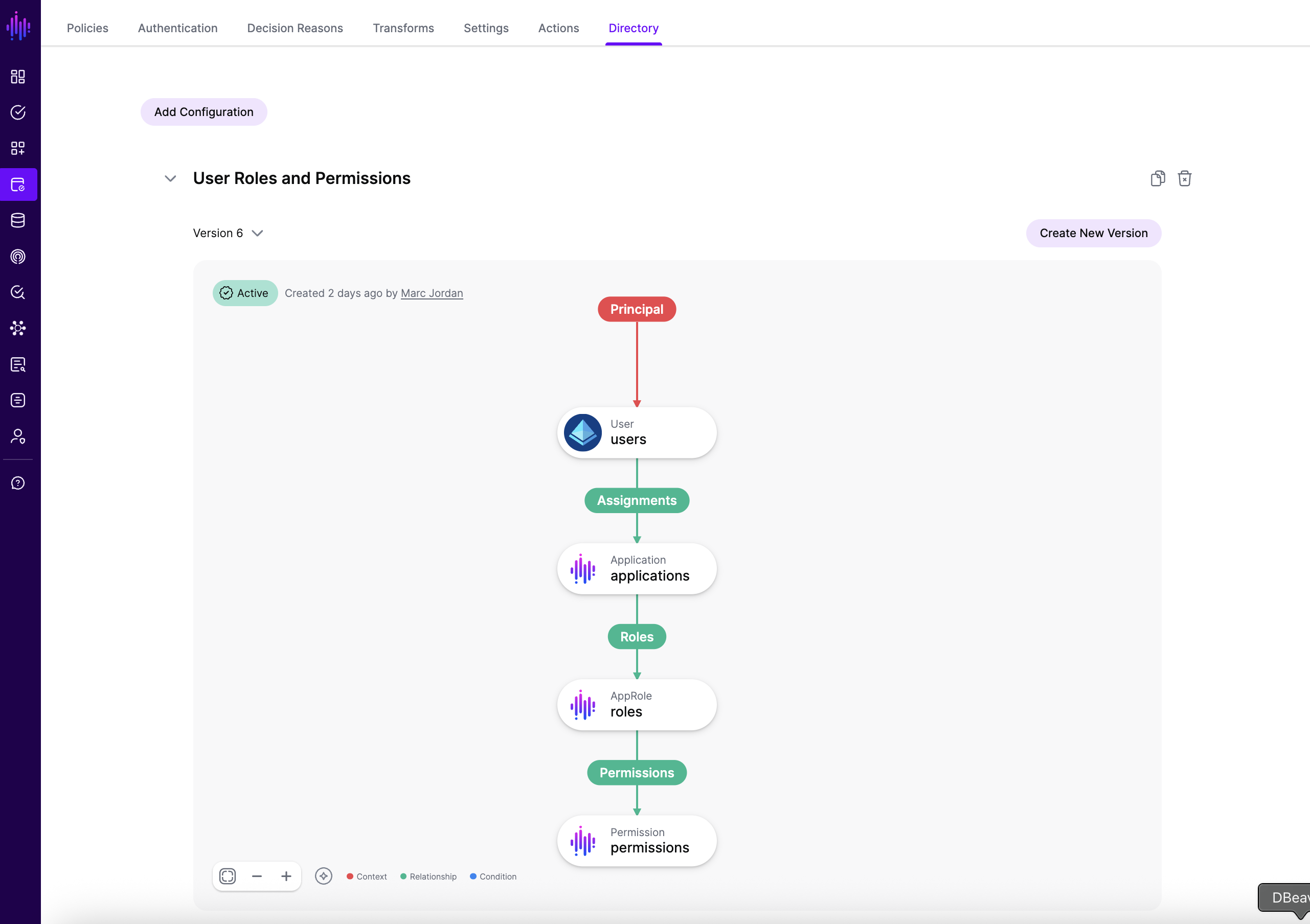
Each directory configuration is versioned, allowing for safe iteration and rollback capabilities.
curl --location 'https://{clientName}.sgnlapis.cloud/access/v2/directory/query?directoryId={directoryId}' \
--header 'Content-Type: application/json' \
--header 'Authorization: Bearer {Protected System Authentication Token}' \
--data-raw '{
"principal": {
"id": "[email protected]",
"ipAddress": "192.168.1.100"
},
"query": {
"action": "access",
"assetId": "corporate-directory"
},
"context": {
"appName": "EmployeePortal",
"requestSource": "web"
}
}'
{
"evaluationDuration": 15,
"issuedAt": "2024-07-24T09:40:24.470844489Z",
"results": [
{
"accountEnabled": true,
"applications": [
{
"appId": "101",
"appName": "HR_System",
"appStatus": "active",
"roles": [
{
"appId": "101",
"roleId": "1001",
"roleName": "Employee",
"roleStatus": "active",
"description": "Standard employee access",
"permissions": [
{
"appId": "101",
"roleId": "1001",
"permissionId": "10001",
"permissionName": "ViewProfile",
"permissionStatus": "active"
},
{
"appId": "101",
"roleId": "1001",
"permissionId": "10002",
"permissionName": "UpdateContact",
"permissionStatus": "active"
}
]
},
{
"appId": "101",
"roleId": "1002",
"roleName": "Manager",
"roleStatus": "active",
"description": "Management privileges",
"permissions": [
{
"appId": "101",
"roleId": "1002",
"permissionId": "10003",
"permissionName": "ViewReports",
"permissionStatus": "active"
}
]
}
],
"systemId": "hr-001"
}
],
"businessPhones": ["+1-555-123-1234"],
"createdDateTime": "2024-01-15T08:30:00Z",
"department": "Engineering",
"displayName": "John Doe",
"givenName": "John",
"id": "550e8400-e29b-41d4-a716-446655440000",
"mail": "[email protected]",
"mailNickname": "john.doe",
"surname": "Doe",
"userPrincipalName": "[email protected]",
"userType": "Member"
}
]
}
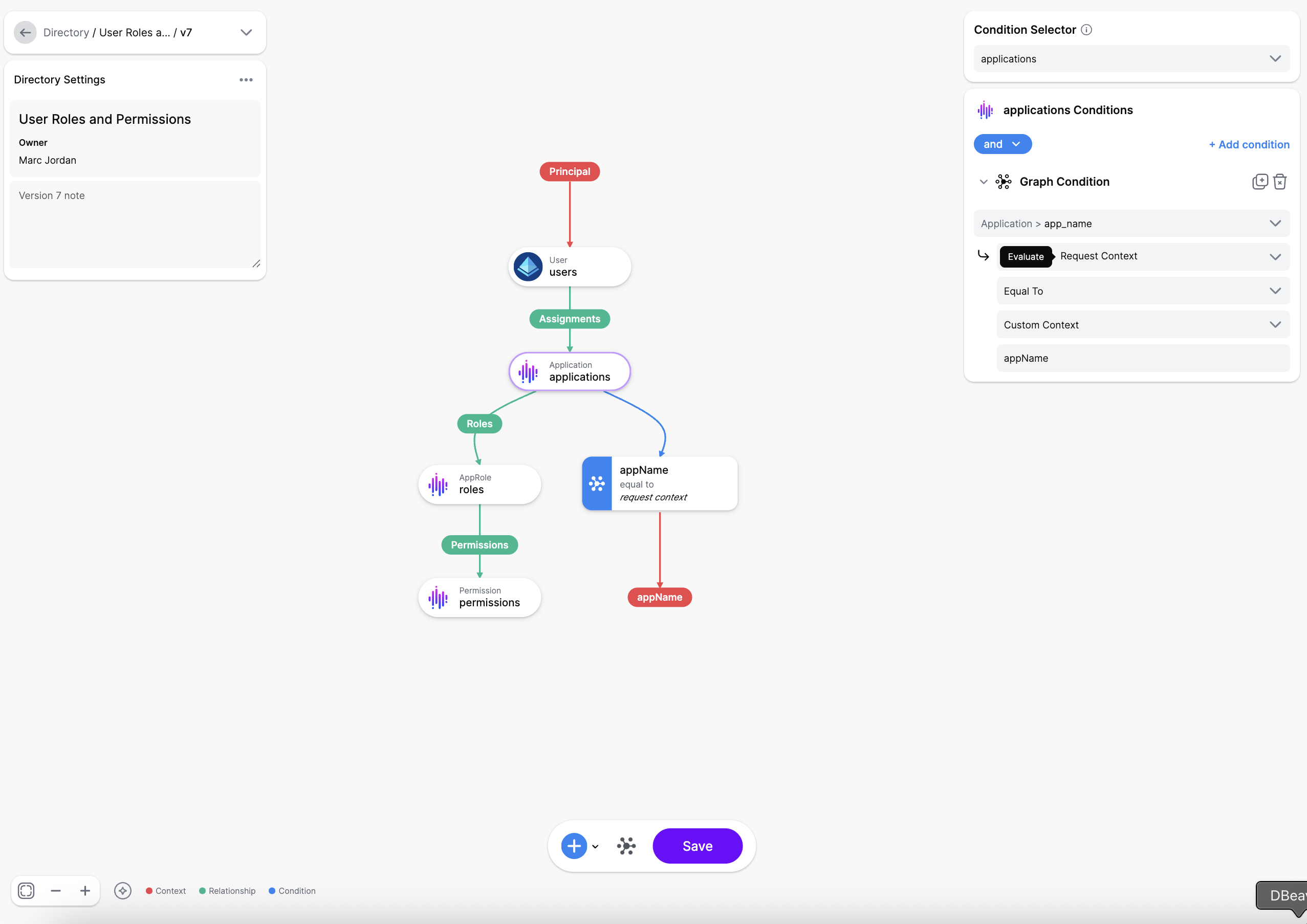
The Directory API supports powerful filtering capabilities through context parameters. You can filter the returned graph structure based on dynamic values passed in the request context. This is an important feature for optimizing response size and ensuring applications receive only relevant data.
curl --location 'https://{clientName}.sgnlapis.cloud/access/v2/directory/query?directoryId={directoryId}' \
--header 'Content-Type: application/json' \
--header 'Authorization: Bearer {Protected System Authentication Token}' \
--data-raw '{
"principal": {
"id": "[email protected]",
"deviceId": "device-12345"
},
"query": {
"action": "login",
"assetId": "application-portal"
},
"context": {
"appName": "HR_System",
"environment": "production"
}
}'
This request would return only the roles and permissions for the “HR_System” application, filtered by the context provided.
You can also customize the format of both the inbound request and response, depending on the system that is calling SGNL. The Directory API supports Custom Transforms, enabling the request and response to be totally customized to match your application’s expected format.
This powerful feature allows you to adapt the Directory API to work seamlessly with existing systems and applications, ensuring compatibility without requiring changes to your existing integrations.
The Directory API is fully policy-aware, meaning it evaluates configured policies before returning directory information. This enables organizations to:
A common policy might deny directory access for compromised identities:
Deny access to the Directory API for any compromised identity
When this policy is active, users flagged as compromised (e.g., by CrowdStrike or other security tools) will receive a 401 Unauthorized response instead of directory data.
All Directory API access requests are automatically logged in SGNL’s Access Logs, providing complete audit trails for compliance and security monitoring. These logs include details about the requesting principal, policy decisions, and access patterns.
IDPs like Okta can use the Directory API to enrich user sessions with detailed role and permission information, enabling more granular authorization decisions at the application level.
Organizations with complex entitlement systems can expose their authorization hierarchies through the Directory API, allowing applications to understand the full context of a user’s permissions.
The Directory API provides a structured way to query and understand user entitlements across systems, supporting audit processes and compliance reporting.
Applications can use the Directory API to dynamically provision user access based on their current entitlements and organizational relationships.
{
"error": {
"code": 401,
"internalCode": "SGNL-40100",
"message": "The user is not authorized to make the request.",
"status": "UNAUTHORIZED"
}
}
The SGNL Directory API documentation can be found on our API Documentation Page.