
Login to the Microsoft Azure Portal and launch the Azure AD Console
From the left navigation pane, select App Registrations
Create a New Registration
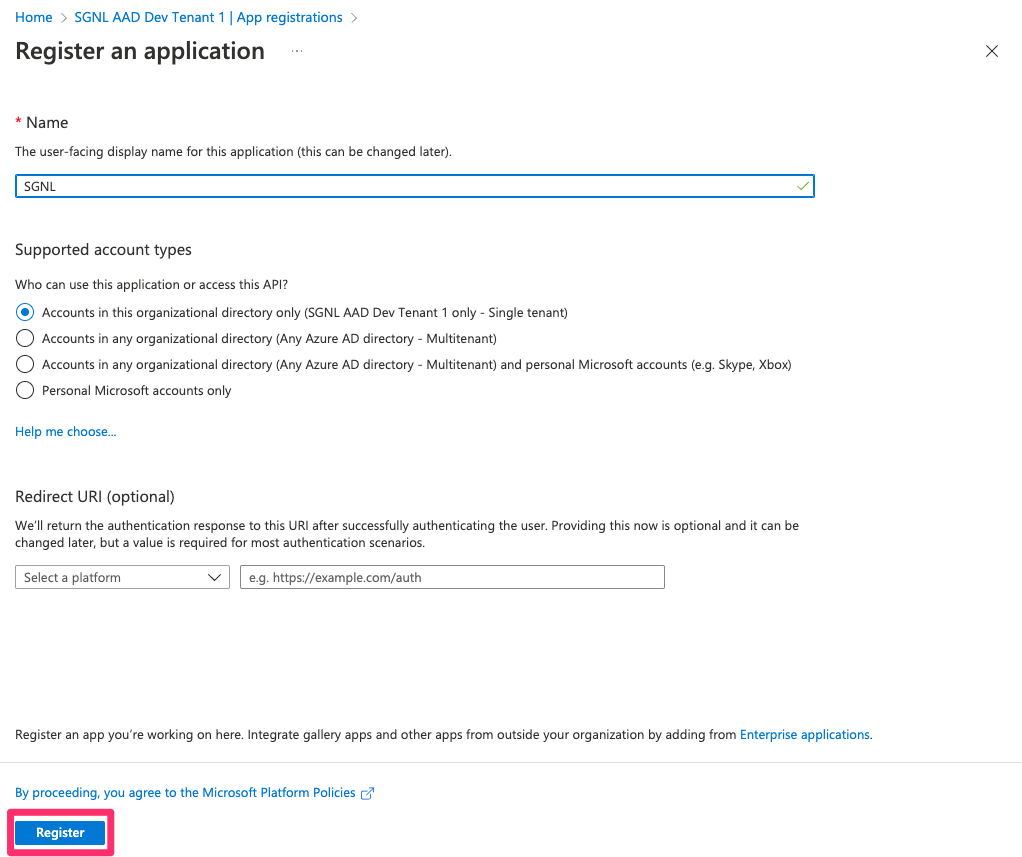
Specify a Name for the App and choose Register
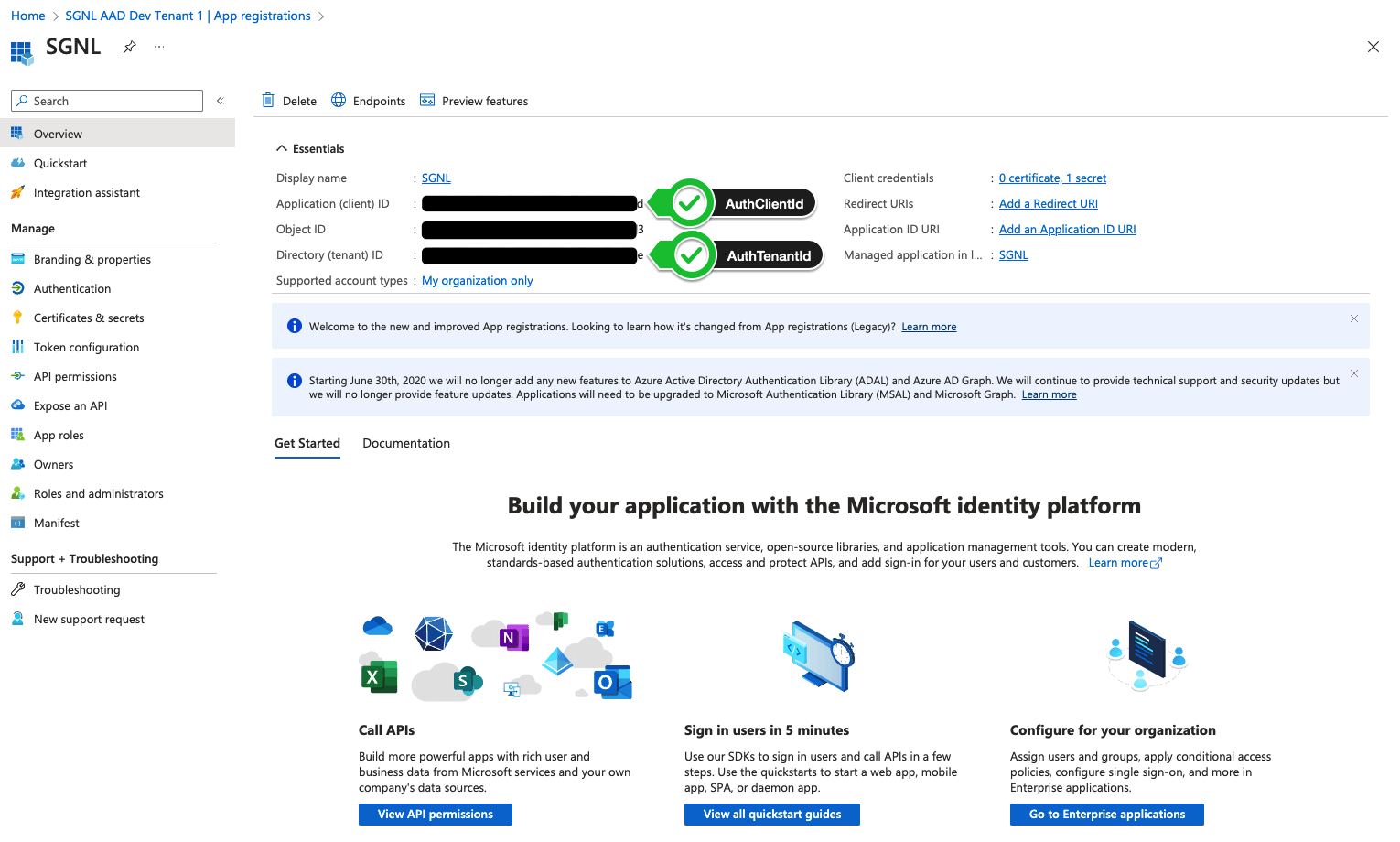
Within the App Registration, note the:
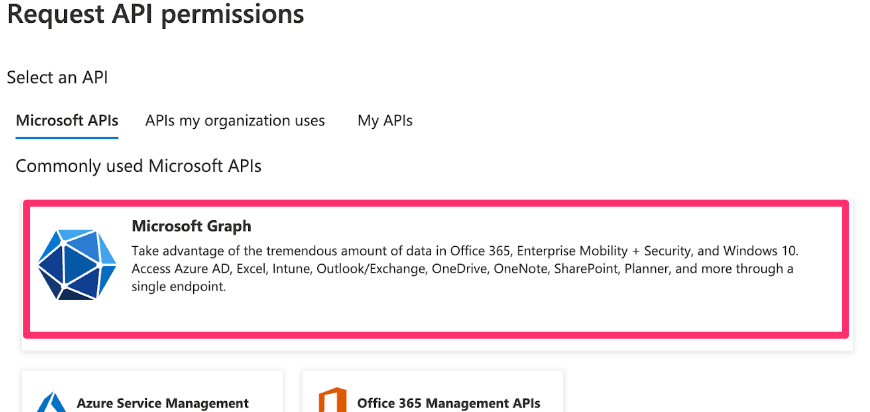
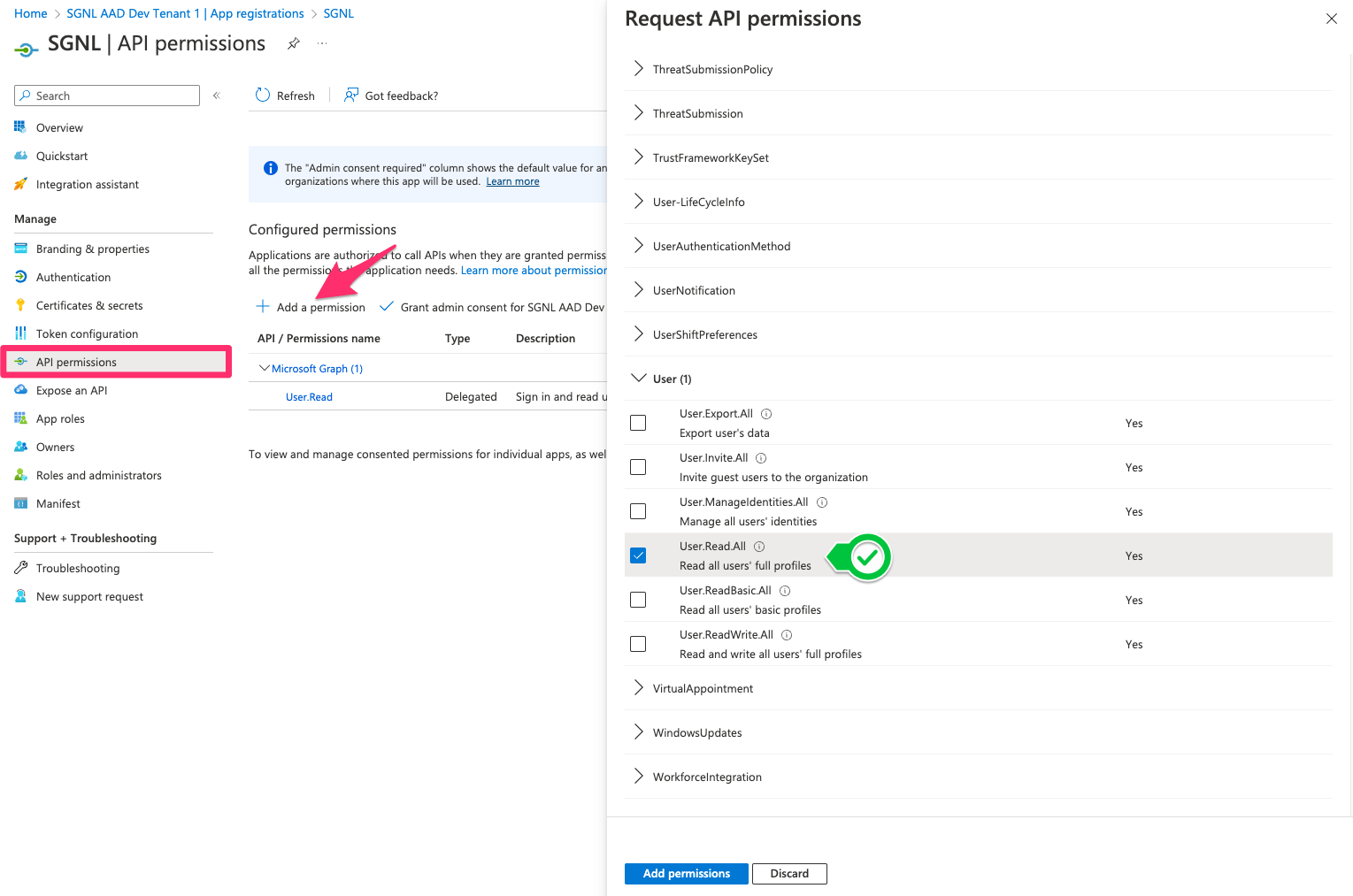
From the API permissions page in the left menu, choose to Add a permission
Select Microsoft Graph
Select “Application Permissions”
Select the below and Add permissions:
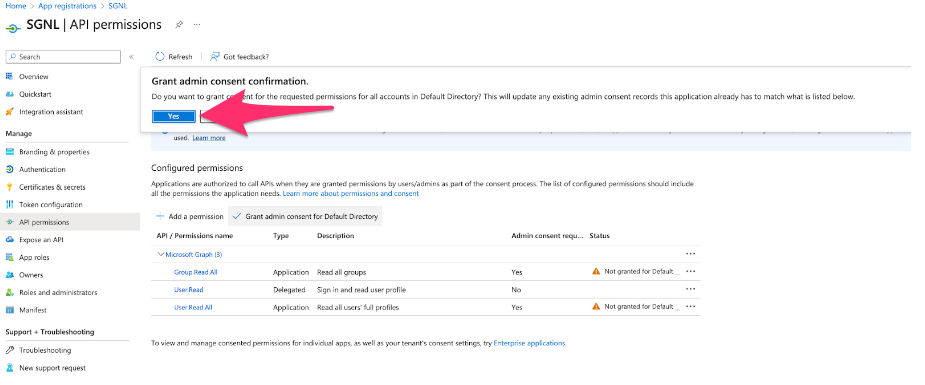
If asked to do so, grant “admin consent”
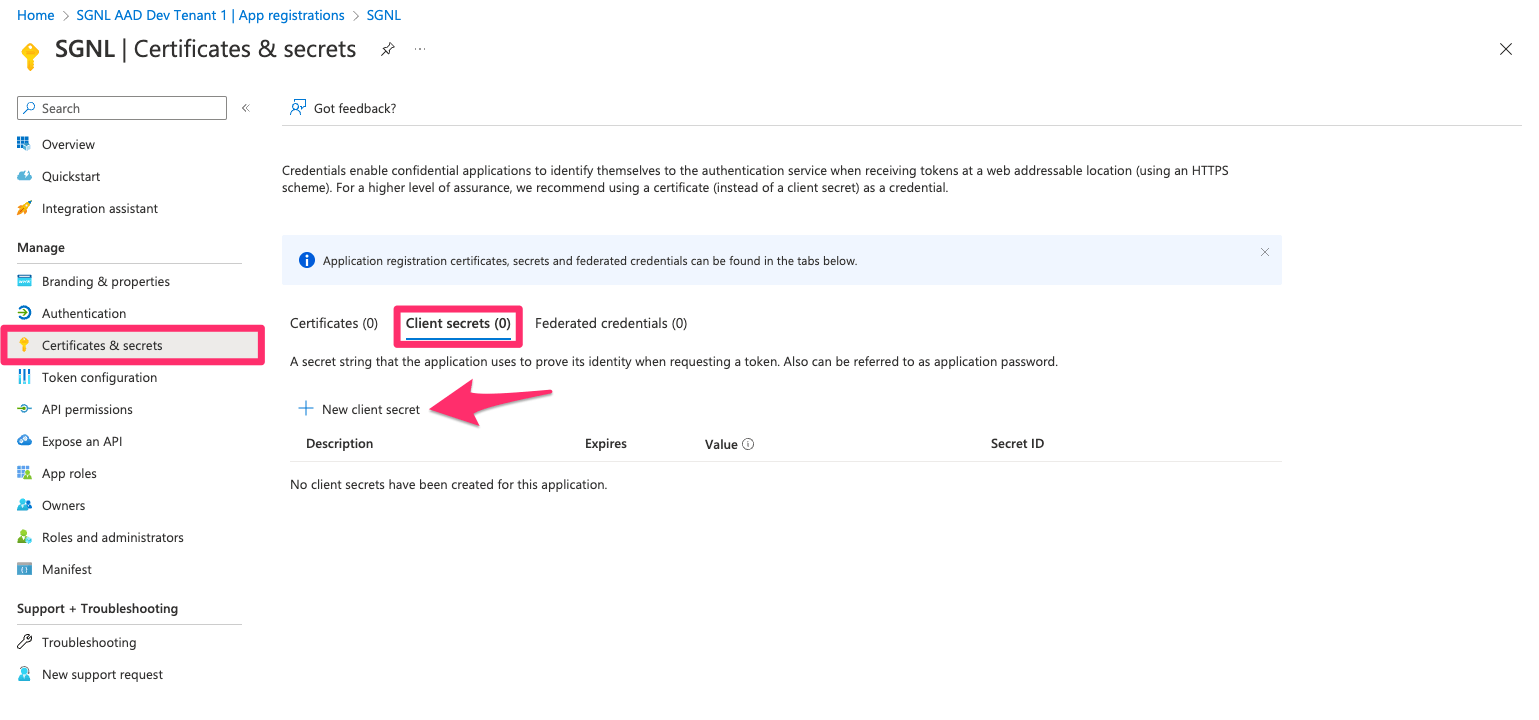
Select Certificates and Secrets from the left menu, select Client secrets, and + New Client Secret
Give the secret a description and expiry (the length of time until a new secret will need to be generated for SGNL to communicate with Azure AD), and select Add
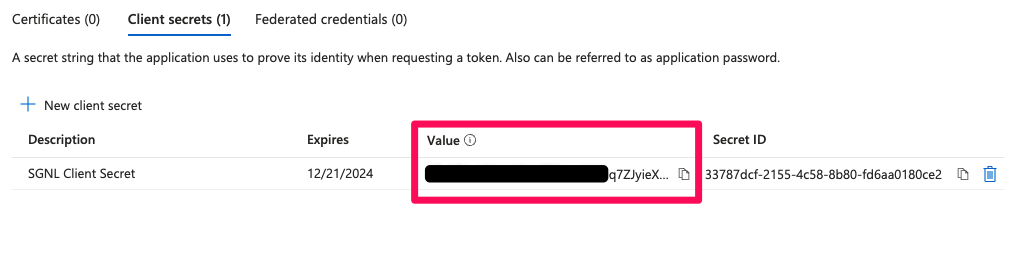
Copy the Value of the secret, this will be required for the SGNL Console (SGNL: AuthClientSecret)
Login to the SGNL Console
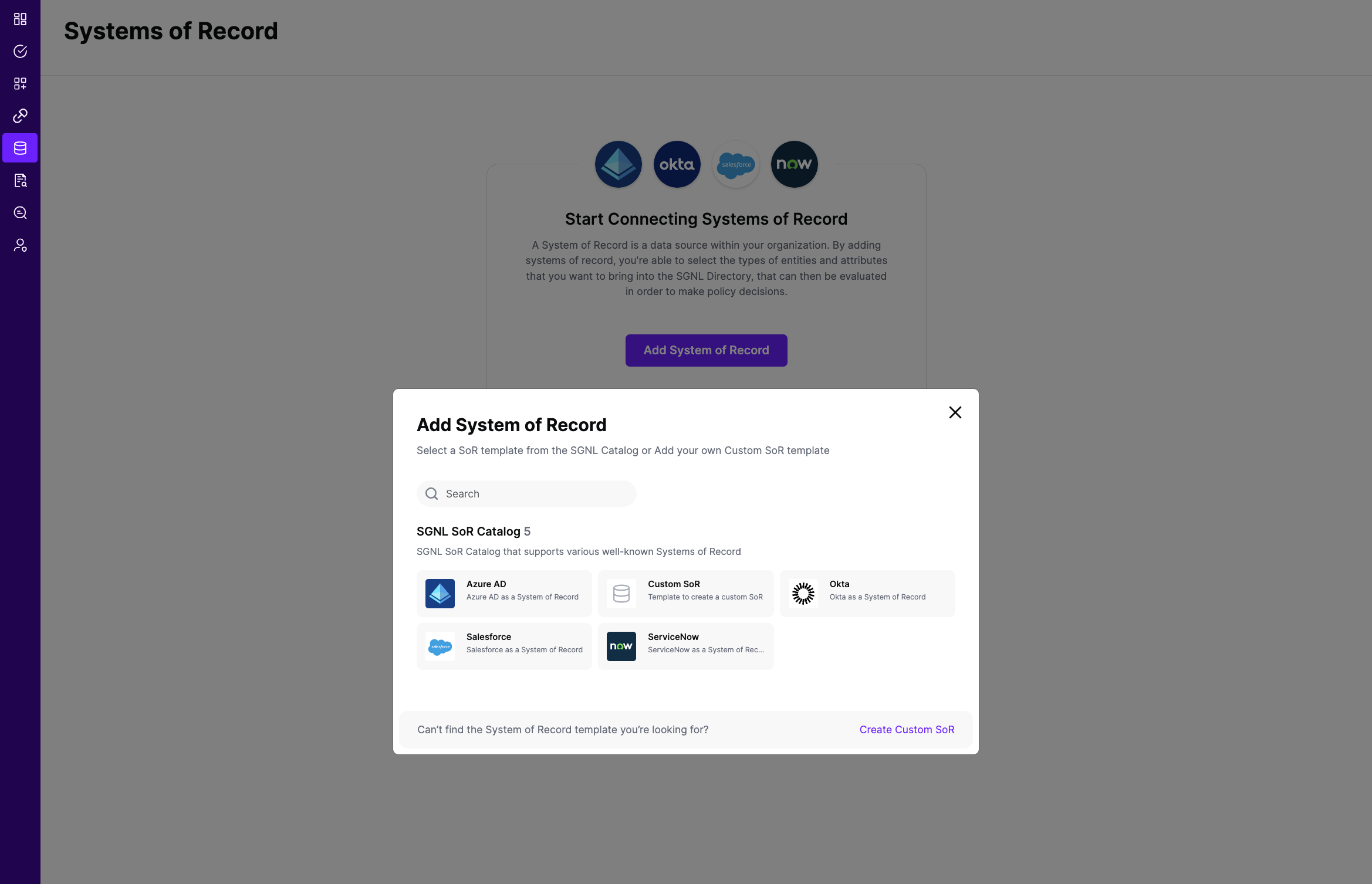
From the left menu, select Data Sources
Add a New Data Source and select Azure Active Directory
Enter the following data into SGNL:
Once configured, click Continue to save your Data Source and move on to configuring Entities
From the Entities tab, click on ‘Edit Attributes’ to select the entities and attributes you will need synchronized into SGNL to be used in your specified SGNL policies
(If applicable) If you will be synchronizing entities and attributes from 2+ different data sources into SGNL to define policies, click on Add join rule to specify the attribute(s) that will join the entities you’ve configured to synchronize from Azure Active Directory to other entities in the SGNL Graph
Save the Configuration