
Policy Snippets and Policy Snippet Versions are critical components in Policy composition. This reference will discuss the scope of policy snippets and importantly, the semantics to be used when creating policy snippet versions that can be used in policies.
Policy Snippets have different scopes, these include:
Policy Snippets are objects in SGNL that group Policy Snippet Versions. Policy Snippets are able to be created and partially updated after creation, however Policy Snippets are not able to be deleted once created.
In order to create a Policy Snippet,
In the left side navigation in the SGNL Console, go to Snippets, and click Add Snippet like so:
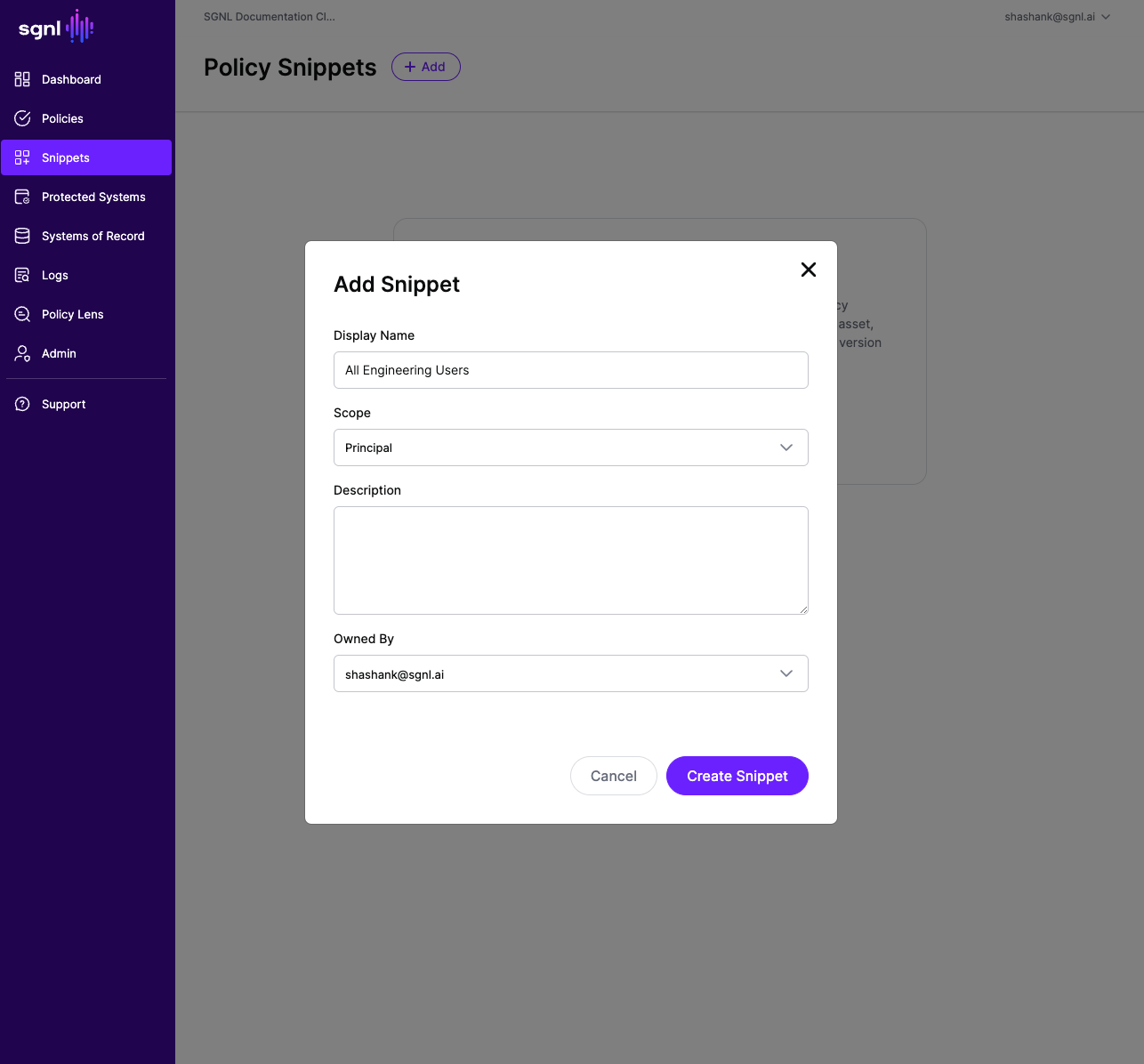
Add the Display Name, select the Scope, add an optional description, and click Save.
In order to use a Policy Snippet, it must have at least one Policy Snippet Versions. Snippet Versions leverage SGNL’s Graph Directory for fast, efficient, and simplified evaluation. In order to create Policy Snippet Versions against entities in the graph, SGNL makes use of Nodes, Relationships, and Conditions to pattern match in the graph.
To create a Snippet Version, click on the Policy Snippet you just created, and click on Create New Version. You should see a page like so:
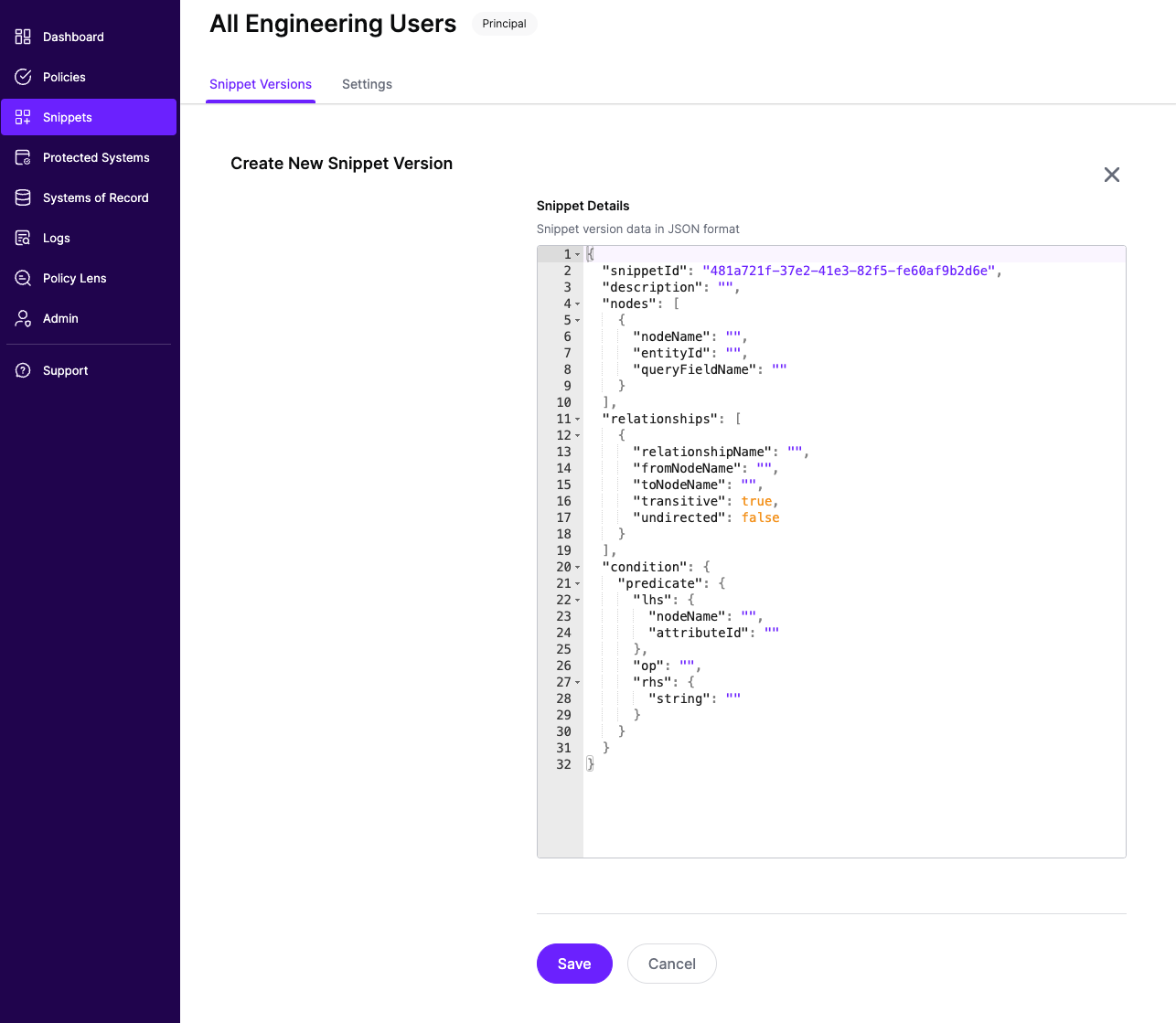
{
"snippetId": "f089c849-e307-4153-bda4-0971200ba35b",
"description": "Description",
"nodes": [{}],
"relationships": [{}],
"condition": {},
"version": 1
}
| Property Name | Property Type | Description |
|---|---|---|
| snippetId | string | The identifier for the Snippet you wish to create this Snippet Version within. The snippetId is already set to the ID of the snippet |
| description | string | A friendly description that describes this version of the Policy Snippet |
| nodes | array of objects | Optional field to describe the types of entities that will be described in your Policy Snippet Version. More information below |
| relationships | array of objects | Optional field to define relationships between nodes used to evaluate the policy. More information below |
| condition | object | Optional field to constrain the search criteria of the nodes that should be evaluated. More information below |
| version | integer | The version for this Snippet Version, must be greater than the latest existing Snippet Version |
Nodes describe the types of entities that will be described in your Policy Snippet Version. They directly reference entities that are synchronized from the various Systems of Record and entities you have configured inside of SGNL.
It is useful to define Nodes when your Policy Snippet Version refers to specific entities as part of the snippet evaluation. For instance, if your Policy Snippet Version evaluates whether an Okta User is from the Engineering Department, create a Node to specify the Okta User node. You can then use the attributeId from the Okta User node you’ve defined to specify a Condition that evaluates whether the user’s profile__department attribute is EqualTo Engineering.
However, Nodes are optional; you do not need to define Nodes if your snippet evaluates whether a principal from any System of Record has privileged access to secure assets following your organizational naming convention (i.e. principalId starts with “privileged-user”).
For example, you might want to use Nodes to reference user entities and group entities in the Policy Snippet Version you are creating from your Okta Tenant.
"nodes": [
{
"nodeName": "user",
"entityId": "{{Id of the Okta User `Entity` in the `Okta` System of Record}}",
"queryFieldName": "principalId"
},
{
"nodeName": "group",
"entityId": "{{Id of the Okta Group `Entity` in the `Okta` System of Record}}"
}
],
| Property Name | Property Type | Description |
|---|---|---|
| entityId | string | The entity identifier for the entity in your System of Record (e.g. Okta User) that you are referencing in the snippet version, e.g. c4194907-ec87-4018-9a82-b84c73b3eb56 |
| nodeName | string | Assign the node you are referencing a name, so that you can refer to it in other parts of the policy snippet version, when defining relationships or conditions |
| queryFieldName | string | (Optional) This is the field name of a property in the access request, that you might want to use as an operand against one of the nodes (i.e. does the principalId in the access request relate to this node) |
Relationships reference the nodes you’ve expressed in the ’nodes’ expression of your Snippet Version in order to define which edges in the graph (the relationships) to traverse in order to evaluate policy.
It is useful to define Relationships when your Policy Snippet Version makes snippet evaluation decisions based on relationships between nodes. For instance, if your Policy Snippet Version evaluates whether an Okta User is a Manager of another Okta User, use Relationships to assess whether the principal requesting access has that relationship.
However, you do not need to define Relationships if your snippet version does not draw upon one of the well-defined relationships that SGNL creates within a System of Record (see table on Relationship Names below for further detail) or a custom relationship that you have defined.
For example, you might want to use Relationships to take the user and group entities you referenced in the ‘nodes’ section of your Snippet Version to evaluate if the calling principal is a direct or indirect member of a group.
"relationships": [
{
"relationshipName": "{{Value of the `name` field on the relationship}}",
"fromNodeName": "user",
"toNodeName": "group",
"transitive": false
}
],
| Property Name | Property Type | Description |
|---|---|---|
| relationshipName | string | Determines the relationship to traverse, this can be one of the well-defined relationships that SGNL creates within a System of Record, the join attribute used for entities of the same type across Systems of Record, or a custom relationship type. |
| fromNodeName | string | The name of the node to start this evaluation from, with a name as declared in the nodes expression in this snippet |
| toNodeName | array of objects | The name of the node to terminate this evaluation, with a name as declared in the nodes expression in this snippet |
| transitive | boolean | Can multiple relationships of this type be traversed to determine whether this snippet matches (e.g. direct member of a group, or indirect via nesting; direct report to a manager or an indirect report via reporting structure) |
| undirected | boolean | Whether a snippet evaluation should match in any direction, thereby ignoring the direction that is configured in the relationship |
Conditions constrain the search criteria of the nodes that should be evaluated as part of the snippet evaluation and of the evaluation of the policy.
Conditions are extremely flexible, but we’ll start with a simple example. Say you want to ensure that a Principal Snippet Version should only be evaluated for users in a certain group, you would specify Node and Relationship fields as we have above, and in the conditions - you would specify a constraint that the group had to have a specific identifier to be matched.
"condition": {
"predicate": {
"lhs": {
"attributeId": "{{objectSID (UUID of the objectSID attribute in the Active Directory SoR, e.g. `a641251d-5917-4700-9617-58acd53961aa`)}}",
"nodeName": "group"
},
"op": "EqualTo",
"rhs": {
"string": "S-1-5-21-2562418665-3218585558-1813906818-1576"
}
}
}
| Property Name | Property Type | Description |
|---|---|---|
| lhs | object | Specifies the “left-hand-side” of the condition evaluation, or the thing that should be compared - this can be any of the comparators detailed below |
| op | string | The operator to use for the condition evaluation, supported operators include: Contains, EndsWith, EqualTo, GreaterThan, GreaterThanOrEqual, LessThan, LessThanOrEqualTo, RegexEqualTo, StartsWith |
| rhs | object | Specifies the “right-hand-side” of the condition evaluation, or the thing that should be compared to - this can be any of the comparators detailed below |
| Comparator | Description |
|---|---|
| queryFieldName | One of the fields in the request to the access service (e.g. “queryFieldName”: “action” ) |
| nodeName, attributeId | Reference to a specific node declared in this snippet (from the nodes above) and an attribute on that node (e.g. "attributeId": {{attributeId}}, "nodeName": "group") |
| boolean | Whether a specific value is true or false |
| date | Evaluates a date in the form of “YYYY-MM-DD” (e.g. "2022-10-18") |
| dateTime | Evaluates a date in the form of “YYYY-MM-DDThh:mm:ssTZD” (e.g. "2022-10-19T05:24:06+00:00") |
| integer | Evaluates an integer (e.g. 12) |
| number | Evaluates a number (e.g. 12.32) |
| string | Evaluates a string (e.g. "S-1-5-21-2562418665-3218585558-1813906818-1576") |
Thus far, we’ve looked only at Conditions that contain a single predicate, but conditions can support multiple predicates that can be evaluated together using additional operands.
| Predicate Operand | Description |
|---|---|
| and | All of the predicates need to be evaluated as true for this policy snippet to match |
| or | Any of the predicates need to be evaluated as true for this policy snippet to match |
| not | These predicates cannot be evaluated as true for this policy snippet to match |
Example using and
The following condition evaluates to True if the principal is in the Engineering department and the Country of Residence is USA. The attributeIds are the UUIDs identifying each of the attributes being evaluated.
"condition": {
"and": [
{
"predicate": {
"lhs": {
"attributeId": "{{profile__department (UUID of the profile__department attribute in the Okta SoR, e.g. `819f2078-6b51-43e8-b3ef-ebbdae499b50`)}}",
"nodeName": "oktaUser"
},
"op": "EqualTo",
"rhs": {
"string": "Engineering"
}
}
},
{
"predicate": {
"lhs": {
"attributeId": "{{profile__countryCode (UUID of the profile__countryCode attribute in the Okta SoR, e.g. `39c1e28c-5ec7-407d-8bf7-f8d1e29dd6d2`)}}",
"nodeName": "oktaUser"
},
"op": "RegexEqualTo",
"rhs": {
"string": "USA"
}
}
}
]
}
Example using or
The following condition evaluates to True if the principal is in the Engineering department OR the Support department. The attributeIds are the UUIDs identifying each of the attributes being evaluated.
"condition": {
"or": [
{
"predicate": {
"lhs": {
"attributeId": "{{profile__department (UUID of the profile__department attribute in the Okta SoR, e.g. `6db0a629-eab7-42b3-b4d3-158e0cfc6519`)}}",
"nodeName": "oktaUser"
},
"op": "EqualTo",
"rhs": {
"string": "Engineering"
}
}
},
{
"predicate": {
"lhs": {
"attributeId": "{{profile__department (UUID of the profile__department attribute in the Okta SoR, e.g. `169272ce-9634-47d7-befe-98ab7e8cce0a`)}}",
"nodeName": "oktaUser"
},
"op": "EqualTo",
"rhs": {
"string": "Support"
}
}
}
]
}
Example using not
The following condition evaluates to True if the asset (Jira Issue) is not in Resolved status. The attributeIds are the UUIDs identifying each of the attributes being evaluated.
"condition": {
"not": {
"predicate": {
"lhs": {
"attributeId": "{{status (UUID of the Jira Issue's status attribute in the Jira SoR, e.g. `b11b5691-51b7-49c8-996e-20bdc55f5aa0`)}}",
"nodeName": "jiraIssue"
},
"op": "EqualTo",
"rhs": {
"string": "Resolved"
}
}
}
}
Principal Snippets define the population of principals (e.g. users, services, robots) that a policy will apply to. It may look at an attribute or relationship of users in order to define a cohort, e.g. All Users in a Corporate Entra ID that have a department of ‘Engineering’, or are in the Entra ID Group with an id of f089c849-e307-4153-bda4-0971200ba35b (representing the Engineering group).
All Principals
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "principalId"
},
"op": "RegexEqualTo",
"rhs": {
"string": ".*"
}
}
},
"description": "All Principals",
"snippetId": "{{your-snippet-id}}"
}
A Principal is a direct member of an Entra ID Group
{
"nodes": [
{
"nodeName": "user",
"entityId": "{{aadUserEntityId (UUID of the User Entity in the Entra ID SoR, e.g. `edd01d13-3f07-4d2f-8a02-68589d150242` )}}",
"queryFieldName": "principalId"
},
{
"nodeName": "group",
"entityId": "{{aadGroupEntityId (UUID of the Group Entity in the Entra ID SoR, e.g. `7c00cd2f-7b9b-4822-beea-f547e1d7440e`)}}"
}
],
"relationships": [
{
"relationshipName": "Group",
"fromNodeName": "user",
"toNodeName": "group",
"transitive": false
}
],
"condition": {
"predicate": {
"lhs": {
"attributeId": "{{objectSID (UUID of the ObjectSid attribute in the Entra ID SoR, e.g. `62351434-f977-4dfa-8a0a-2cbe6acf6ca2`)}}",
"nodeName": "group"
},
"op": "EqualTo",
"rhs": {
"string": "S-1-5-21-2562418665-3218585558-1813906818-1576"
}
}
},
"description": "Belongs to our Entra ID Employee Group",
"snippetId": "{{your-snippet-id}}",
"version": 1
}
Principal has a title of Admin or Developer as provided by Okta
{
"nodes": [
{
"nodeName": "oktaUser",
"entityId": "{{oktaUserEntityId (UUID of the User Entity in the Okta SoR, e.g. `0d4e1c92-7613-4c27-811d-8b6af887c91e`)}}",
"queryFieldName": "principalId"
}
],
"condition": {
"or": [
{
"predicate": {
"lhs": {
"attributeId": "{{profile__title (UUID of the profile__title attribute in the Okta User Entity, e.g. `d70fbcde-dcc4-4624-ad03-03ecb0590774`)}}",
"nodeName": "oktaUser"
},
"op": "EqualTo",
"rhs": {
"string": "admin"
}
}
},
{
"predicate": {
"lhs": {
"attributeId": "{{profile__title (UUID of the profile__title attribute in the Okta User Entity, e.g. `0281acfd-8c5a-4079-acc1-2c07cf530fe4`)}}",
"nodeName": "oktaUser"
},
"op": "EqualTo",
"rhs": {
"string": "developer"
}
}
}
]
},
"description": "User is an Admin or a Developer",
"snippetId": "{{your-snippet-id}}",
"version": 1
}
User in Customer Support
UUID Reference:
- Entities:
- Okta User: cdeb4879-b83f-46af-b57e-de114b011fd3
- Attributes:
- Okta User profile__title: 5f7c716f-756a-4100-a403-ffd0f3fff86f
{
"condition": {
"predicate": {
"lhs": {
"attributeId": "5f7c716f-756a-4100-a403-ffd0f3fff86f",
"nodeName": "oktaUser"
},
"op": "EqualTo",
"rhs": {
"string": "Customer Support"
}
}
},
"description": "User in Customer Support",
"nodes": [
{
"entityId": "cdeb4879-b83f-46af-b57e-de114b011fd3",
"nodeName": "oktaUser",
"queryFieldName": "principalId"
}
],
"relationships": [],
"snippetId": "{{your-snippet-id}}"
}
User is a Member of the Engineering EntraID Group with a UUID of 14bce36c-7931-43e7-a2d8-a93207f6df15
UUID Reference:
- Entities:
- Entra ID Group: 71d12aec-fac4-4fc5-b196-2d48a5d21556
- Entra ID User: b4139d04-3945-42e9-bc0e-326e91bd0d54
- Attributes:
- Entra ID Group `id`: ce9d8691-aef4-4a18-808e-45013aef8164
{
"condition": {
"predicate": {
"lhs": {
"attributeId": "ce9d8691-aef4-4a18-808e-45013aef8164",
"nodeName": "entraGroup"
},
"op": "EqualTo",
"rhs": {
"string": "14bce36c-7931-43e7-a2d8-a93207f6df15"
}
}
},
"description": "User is a Member of an EntraID Group with a specific UUID",
"nodes": [
{
"entityId": "b4139d04-3945-42e9-bc0e-326e91bd0d54",
"nodeName": "entraUser",
"queryFieldName": "principalId"
},
{
"entityId": "71d12aec-fac4-4fc5-b196-2d48a5d21556",
"nodeName": "entraGroup"
}
],
"relationships": [
{
"fromNodeName": "entraUser",
"relationshipName": "UserGroup",
"toNodeName": "entraGroup",
"transitive": false,
"undirected": false
}
],
"snippetId": "{{your-snippet-id}}"
}
Principal’s Crowdstrike User Risk is High
UUID Reference:
- Entities:
- Crowdstrike User: b4139d04-3945-42e9-bc0e-326e91bd0d54
- Attributes:
- Crowdstrike User `riskLevel`: 4e6b8c6a-6171-4126-b080-f2358a586822
{
"condition": {
"predicate": {
"lhs": {
"attributeId": "4e6b8c6a-6171-4126-b080-f2358a586822",
"nodeName": "crowdStrikeUser"
},
"op": "EqualTo",
"rhs": {
"string": "HIGH"
}
}
},
"description": "User Risk is High as determined by Crowdstrike User properties",
"id": "f652c0b3-d25b-4b3a-8b87-85d847af4de4",
"nodes": [
{
"entityId": "2b3c89b5-67c1-49df-8cfd-9677f76de774",
"nodeName": "crowdStrikeUser",
"queryFieldName": "principalId"
}
],
"relationships": [],
"snippetId": "{{your-snippet-id}}"
}
Action Snippets define the actions that SGNL receives from your Protected System at the Access Service. These might include simple actions such as “read” or “write”, or more complex actions such as “issue refund” or “createUser”.
Any Action
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "action"
},
"op": "RegexEqualTo",
"rhs": {
"string": ".*"
}
}
},
"description": "Any Action",
"snippetId": "{{your-snippet-id}}"
}
Assume Role
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "action"
},
"op": "EqualTo",
"rhs": {
"string": "AssumeRole"
}
}
},
"description": "The AssumeRole Action",
"snippetId": "{{your-snippet-id}}"
}
Login Action
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "action"
},
"op": "EqualTo",
"rhs": {
"string": "login"
}
}
},
"version": 1,
"description": "Perform a Login Action",
"snippetId": "{{your-snippet-id}}"
}
Read Action
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "action"
},
"op": "EqualTo",
"rhs": {
"string": "read"
}
}
},
"version": 1,
"description": "Perform a Read Action",
"snippetId": "{{your-snippet-id}}"
}
Asset Snippets define the resource(s) that need protecting within a specific Protected System or across many Protected Systems. These may be individual entitlements, customers, accounts, products, or something else. Asset-scoped snippets can increase the specificity of policies, e.g. Customer data for customers with more than 10,000 employees.
All Assets
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "assetId"
},
"op": "RegexEqualTo",
"rhs": {
"string": ".*"
}
}
},
"description": "All Assets",
"snippetId": "{{your-snippet-id}}"
}
Production Assets
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "assetId"
},
"op": "StartsWith",
"rhs": {
"string": "production-"
}
}
},
"description": "Production Assets",
"snippetId": "{{your-snippet-id}}"
}
Customer Salesforce Accounts
{
"nodes": [
{
"queryFieldName": "assetId",
"entityId": "{{sfdcAccountEntityId (UUID of the Account Entity in the Salesforce SoR, e.g. `1309c59f-825d-4b60-92e5-7b7e6afc1859`)}}",
"nodeName": "account"
}
],
"condition": {
"predicate": {
"lhs": {
"attributeId": "{{Type (UUID of the Type attribute in the Salesforce Account Entity, e.g. `ee654c33-c8bb-4482-8848-de66042b5835`)}}",
"nodeName": "account"
},
"op": "EqualTo",
"rhs": {
"string": "Customer"
}
}
},
"description": "Salesforce Customer Accounts",
"snippetId": "{{your-snippet-id}}",
"version": 1
}
Sensitive Infrastructure Assets
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "assetId"
},
"op": "StartsWith",
"rhs": {
"string": "customer-prod-"
}
}
},
"description": "Production Assets owned by a Customer",
"snippetId": "{{your-snippet-id}}",
"version": 1
}
Condition Snippets define the conditions with which to allow or deny. Condition snippets might look to ensure that a given principal has an appropriate business justification (e.g. through a ServiceNow Case assigned for a given customer), or might look to ensure the user is in the right location, on a trusted device.
ServiceNow User has a ServiceNow Case Assigned
UUID Reference:
- Entities:
- ServiceNow CSM User: 504dea26-29df-4ae6-968f-b13e9bc70082
- ServiceNow CSM Case: 6750bf5a-a762-4737-a055-bc2c4abadaa9
{
"description": "ServiceNow User has a ServiceNow Case Assigned",
"nodes": [
{
"entityId": "6750bf5a-a762-4737-a055-bc2c4abadaa9",
"nodeName": "serviceNowCSMCase"
},
{
"entityId": "504dea26-29df-4ae6-968f-b13e9bc70082",
"nodeName": "serviceNowCSMUser",
"queryFieldName": "principalId"
}
],
"relationships": [
{
"fromNodeName": "serviceNowCSMCase",
"relationshipName": "AssignedTo",
"toNodeName": "serviceNowCSMUser",
"transitive": false,
"undirected": false
}
],
"snippetId": "{{your-snippet-id}}"
}
ServiceNow User has an Active ServiceNow Case Assigned for the Account Asset
UUID Reference:
- Entities:
- ServiceNow CSM User: 504dea26-29df-4ae6-968f-b13e9bc70082
- ServiceNow CSM Case: 6750bf5a-a762-4737-a055-bc2c4abadaa9
- ServiceNow CSM Account: 30b09160-e827-45a6-ac50-37a9c990567c
{
"description": "ServiceNow User has an Active ServiceNow Case Assigned for the Account Asset",
"nodes": [
{
"entityId": "6750bf5a-a762-4737-a055-bc2c4abadaa9",
"nodeName": "serviceNowCSMCase"
},
{
"entityId": "504dea26-29df-4ae6-968f-b13e9bc70082",
"nodeName": "serviceNowCSMUser",
"queryFieldName": "principalId"
},
{
"entityId": "30b09160-e827-45a6-ac50-37a9c990567c",
"nodeName": "serviceNowCSMAccount",
"queryFieldName": "assetId"
}
],
"relationships": [
{
"fromNodeName": "serviceNowCSMCase",
"relationshipName": "AssignedTo",
"toNodeName": "serviceNowCSMUser",
"transitive": false,
"undirected": false
},
{
"fromNodeName": "serviceNowCSMCase",
"relationshipName": "Account",
"toNodeName": "serviceNowCSMAccount",
"transitive": false,
"undirected": false
}
],
"snippetId": "{{your-snippet-id}}"
}
During Business Hours in Chicago, IL
{
"condition": {
"and": [
{
"predicate": {
"lhs": {
"expr": {
"lhs": {
"expr": {
"lhs": {
"queryFieldName": "time.now"
},
"op": "ToTimezone",
"rhs": {
"string": "America/Chicago"
}
}
},
"op": "GetField",
"rhs": {
"string": "Hour"
}
}
},
"op": "GreaterThanOrEqualTo",
"rhs": {
"integer": 6
}
}
},
{
"predicate": {
"lhs": {
"expr": {
"lhs": {
"expr": {
"lhs": {
"queryFieldName": "time.now"
},
"op": "ToTimezone",
"rhs": {
"string": "America/Chicago"
}
}
},
"op": "GetField",
"rhs": {
"string": "Hour"
}
}
},
"op": "LessThanOrEqualTo",
"rhs": {
"integer": 18
}
}
},
{
"predicate": {
"lhs": {
"expr": {
"lhs": {
"expr": {
"lhs": {
"queryFieldName": "time.now"
},
"op": "ToTimezone",
"rhs": {
"string": "America/Chicago"
}
}
},
"op": "GetField",
"rhs": {
"string": "DayOfWeek"
}
}
},
"op": "LessThanOrEqualTo",
"rhs": {
"integer": 5
}
}
}
]
},
"description": "During Business Hours - Monday to Friday",
"nodes": [],
"relationships": [],
"snippetId": "{{your-snippet-id}}"
}
Current Time is within an Active ServiceNow Change Window assigned to the Principal
UUID Reference:
- Entities:
- ServiceNow ITSM User: 57dafe75-3c3f-4805-870a-9656bf33bd51
- ServiceNow ITSM Change Request: bb353069-7291-414a-91c6-6a4b44a09d1d
- Attributes:
- ServiceNow ITSM Change Request `start_date`: 0fa68f90-7a7f-48c6-b6c0-cfd7944ae071
- ServiceNow ITSM Change Request `end_date`: 781160e3-a12a-42da-91e6-37c9a4eed8d8
{
"condition": {
"and": [
{
"predicate": {
"lhs": {
"attributeId": "0fa68f90-7a7f-48c6-b6c0-cfd7944ae071",
"nodeName": "serviceNowITSMChangeRequest"
},
"op": "LessThanOrEqualTo",
"rhs": {
"queryFieldName": "time.now"
}
}
},
{
"predicate": {
"lhs": {
"attributeId": "781160e3-a12a-42da-91e6-37c9a4eed8d8",
"nodeName": "ServiceNowITSMChangeRequest"
},
"op": "GreaterThan",
"rhs": {
"queryFieldName": "time.now"
}
}
}
]
},
"description": "Current Time is within an Active ServiceNow Change Window assigned to the Principal",
"id": "73b203a7-4ead-4be2-b02e-b3bfdad56b59",
"nodes": [
{
"entityId": "57dafe75-3c3f-4805-870a-9656bf33bd51",
"nodeName": "serviceNowITSMUser",
"queryFieldName": "principalId"
},
{
"entityId": "bb353069-7291-414a-91c6-6a4b44a09d1d",
"nodeName": "serviceNowITSMChangeRequest"
}
],
"relationships": [
{
"fromNodeName": "serviceNowITSMChangeRequest",
"relationshipName": "AssignedToUser",
"toNodeName": "serviceNowITSMUser",
"transitive": false,
"undirected": false
}
],
"snippetId": "{{your-snippet-id}}"
}
(note: for more details on Location or Temporal Snippets, see our Advanced Snippet Reference)
Principal is physically located in the United States
{
"condition": {
"predicate": {
"lhs": {
"queryFieldName": "principal.ipAddress.location.country"
},
"op": "EqualTo",
"rhs": {
"string": "US"
}
}
},
"description": "User is physically located in the United States",
"nodes": [],
"relationships": [],
"snippetId": "{{your-snippet-id}}"
}
User is assigned to a ServiceNow Case that belongs to a requested Customer Record
{
"nodes": [
{
"entityId": "{{snowUserEntityId (UUID of the User Entity in ServiceNow SoR, e.g. `e0fea67f-5697-419c-b0d5-a2bd499b9523`)}}",
"nodeName": "snowUser",
"queryFieldName": "principalId"
},
{
"entityId": "{{snowCaseEntityId (UUID of the Case Entity in the ServiceNow SoR, e.g. `afec91bf-2c78-4839-bb03-b70c2f1ae634`)}}",
"nodeName": "snowCase"
},
{
"entityId": "{{snowAccountEntityId (UUID of the Account Entity in the ServiceNow SoR, e.g. `47b27da9-05fe-4ab4-b986-a01e705e3e06`)}}",
"nodeName": "snowAccount",
"queryFieldName": "assetId"
}
],
"relationships": [
{
"relationshipName": "AssignedTo",
"fromNodeName": "snowCase",
"toNodeName": "snowUser"
},
{
"relationshipName": "Account",
"fromNodeName": "snowCase",
"toNodeName": "snowAccount"
}
],
"condition": {
"predicate": {
"lhs": {
"attributeId": "active",
"nodeName": "snowCase"
},
"op": "EqualTo",
"rhs": {
"boolean": true
}
}
},
"description": "User is assigned active case for the customer",
"snippetId": "{{your-snippet-id}}",
"version": 1
}
The Principal is a Manager of a ServiceNow Group
{
"nodes": [
{
"entityId": "{{snowUserEntityId (UUID of the User Entity in ServiceNow SoR, e.g. `f6fe6192-c3b9-43a2-8b39-d44c1f02504e`)}}",
"nodeName": "snowUser",
"queryFieldName": "principalId"
},
{
"entityId": "{{snowGroupEntityId (UUID of the Group Entity in ServiceNow SoR, e.g. `5ccc5c47-5e81-4f76-9b16-ed224be4e546`)}}",
"nodeName": "snowGroup"
}
],
"relationships": [
{
"relationshipName": "Manager",
"fromNodeName": "snowGroup",
"toNodeName": "snowUser"
}
],
"description": "Group Manager",
"snippetId": "{{your-snippet-id}}",
"version": 1
}