Protected Systems are applications, services, or infrastructure that you want to protect with SGNL. In this guide, we’ll explore using one of SGNL’s SDK as the enforcement point for policy decisions made in the SGNL Platform. For a complete overview of how to evaluate access in your application or service from a SGNL SDK, visit our developer documentation.
Your application need not know about the policies, systems of record, or any of the data in SGNL - it simply needs to pass to SGNL:
Authentication ensures that only authorized systems can make requests into SGNL, as well as verifying the identity of an integration in order to effectively evaluate Policies - to access Authentication settings, open your Integration and select the Authentication tab
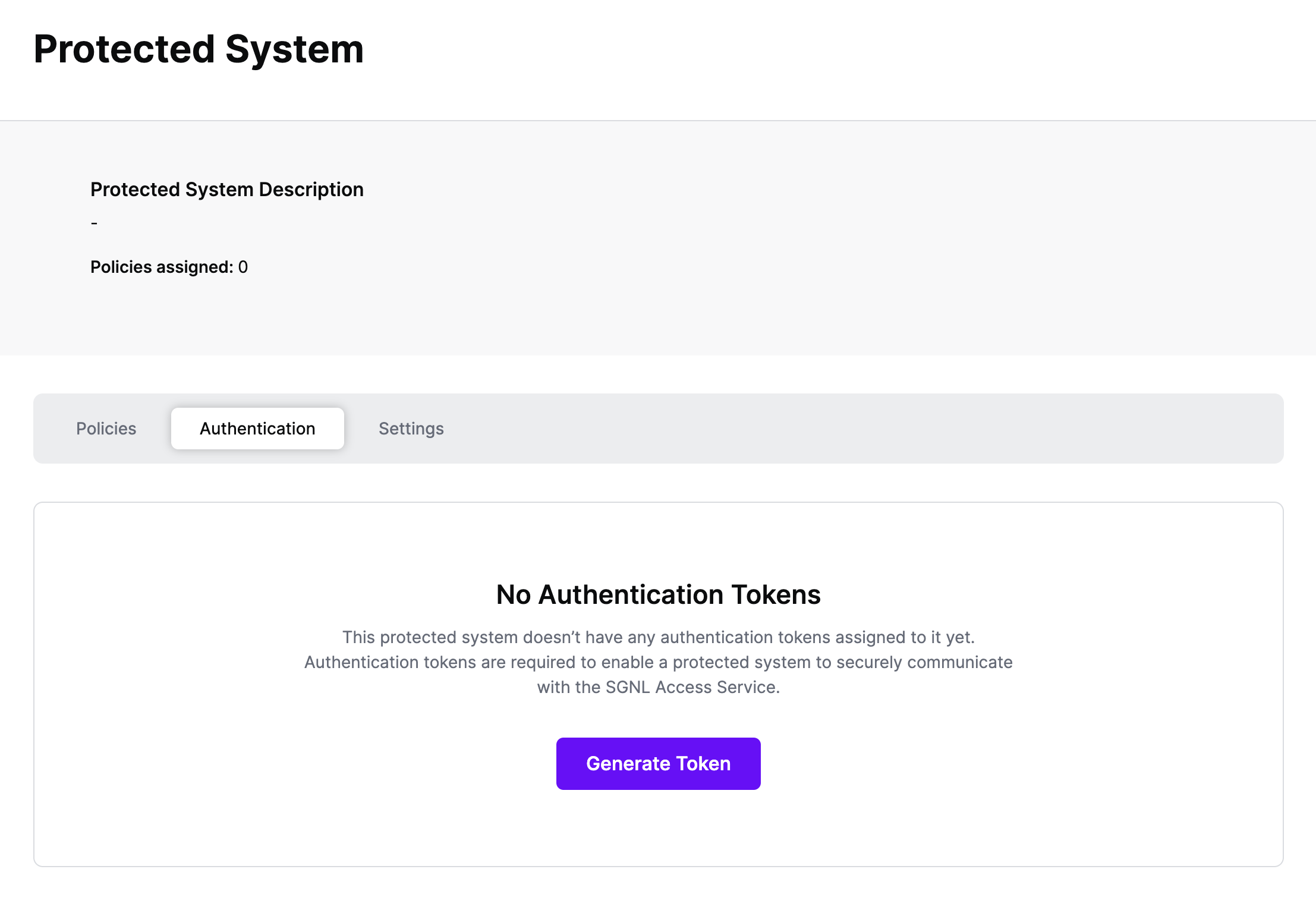
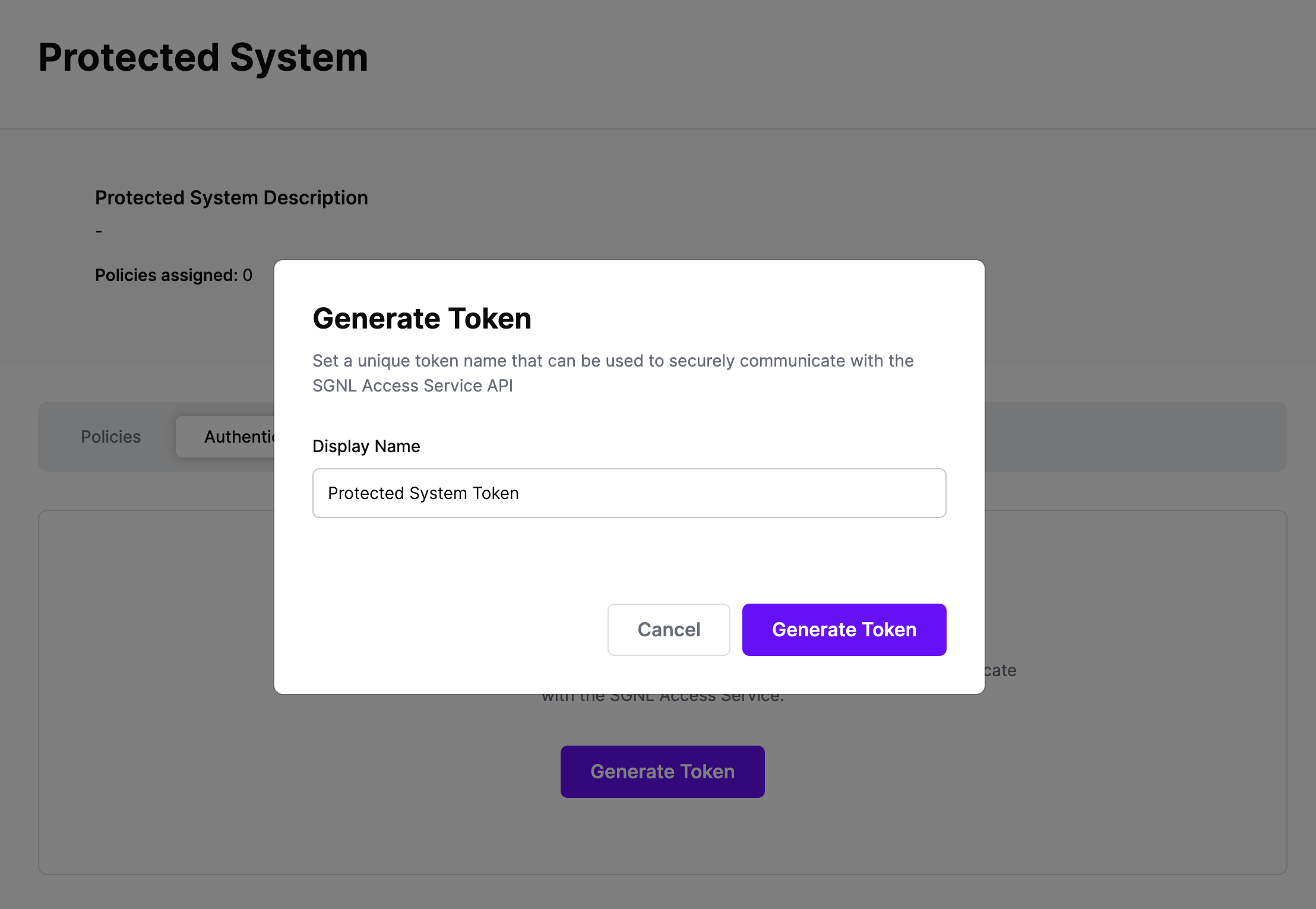
Click Generate Token
Give your token a descriptive name so that you know how it’s being used in the future and click to Generate Token
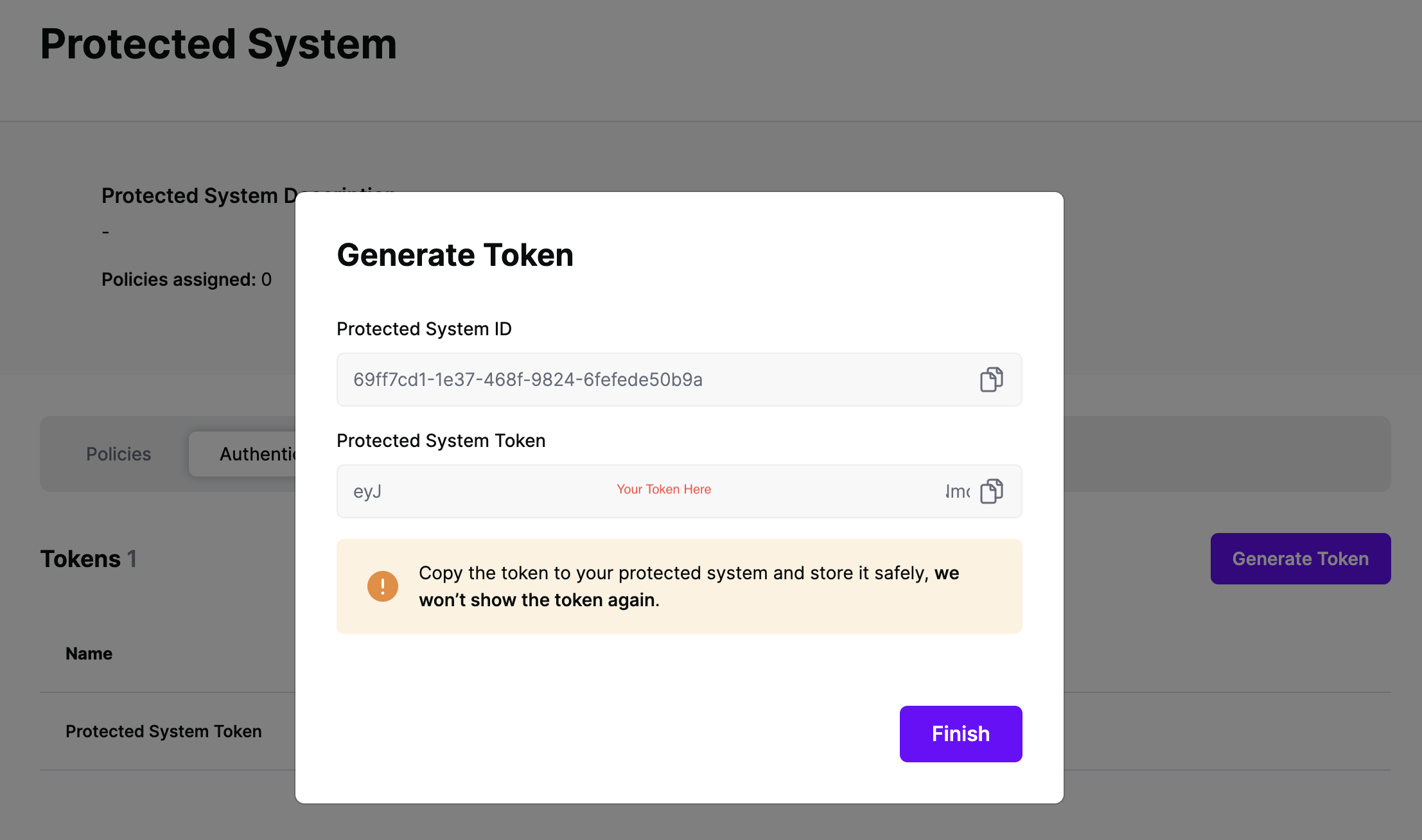
On the next screen, copy the token - this will be used in your protected system to make access requests to SGNL using the SGNL Access Service API
Note: The value of this token is not available again after this screen, so ensure you securely store it for steps later in this guide
The SGNL Client SDKs help to ease the burden of calling the SGNL Access APIs. These SDKs are available in a collection of languages to support whatever project you’re working on. For complete documentation on the SGNL Access API, visit our developer documentation.
SGNL Client SDKs act as the enforcement point inside of your application. It’s recommended that prior to making a request for sensitive data or assets, you first use the SGNL SDK to determine whether the access should be permitted or otherwise.
npm install sgnl --save{
"principal": {
"id": "alice.wu@sgnl.ai",
"ipAddress": "125.23.53.6",
"deviceId": "48:65:ee:17:7e:0b"
},
"queries": [
{
"action": "read",
"assetId": "001Hn00001toN3hIAE"
},
{
"action": "write",
"assetId": "001Hn00001toN3hIAE"
},
{
"action": "read",
"assetId": "002Cn00221xoa3YMPO"
}
]
}
{
"issuedAt": "2023-06-24T22:06:54.530672786Z",
"principalId": "alice.wu@sgnl.ai",
"decisions": [
{
"action": "read",
"assetId": "001Hn00001toN3hIAE",
"decision": "Allow"
},
{
"action": "write",
"assetId": "001Hn00001toN3hIAE",
"decision": "Deny"
},
{
"action": "read",
"assetId": "002Cn00221xoa3YMPO",
"decision": "Allow"
}
],
"evaluationDuration": 8
}
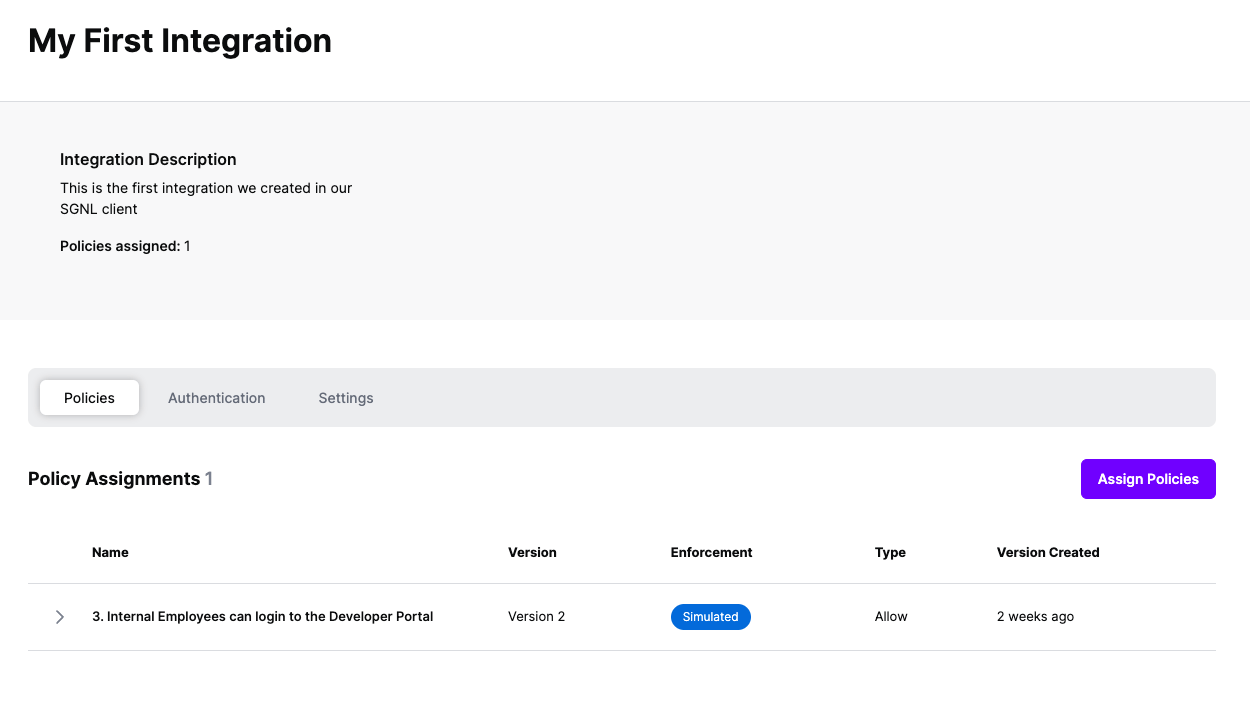
Once the Integration is created, you can start assigning versions of Policies to the integration - to get started, select Policies from the tabs in your newly created integration
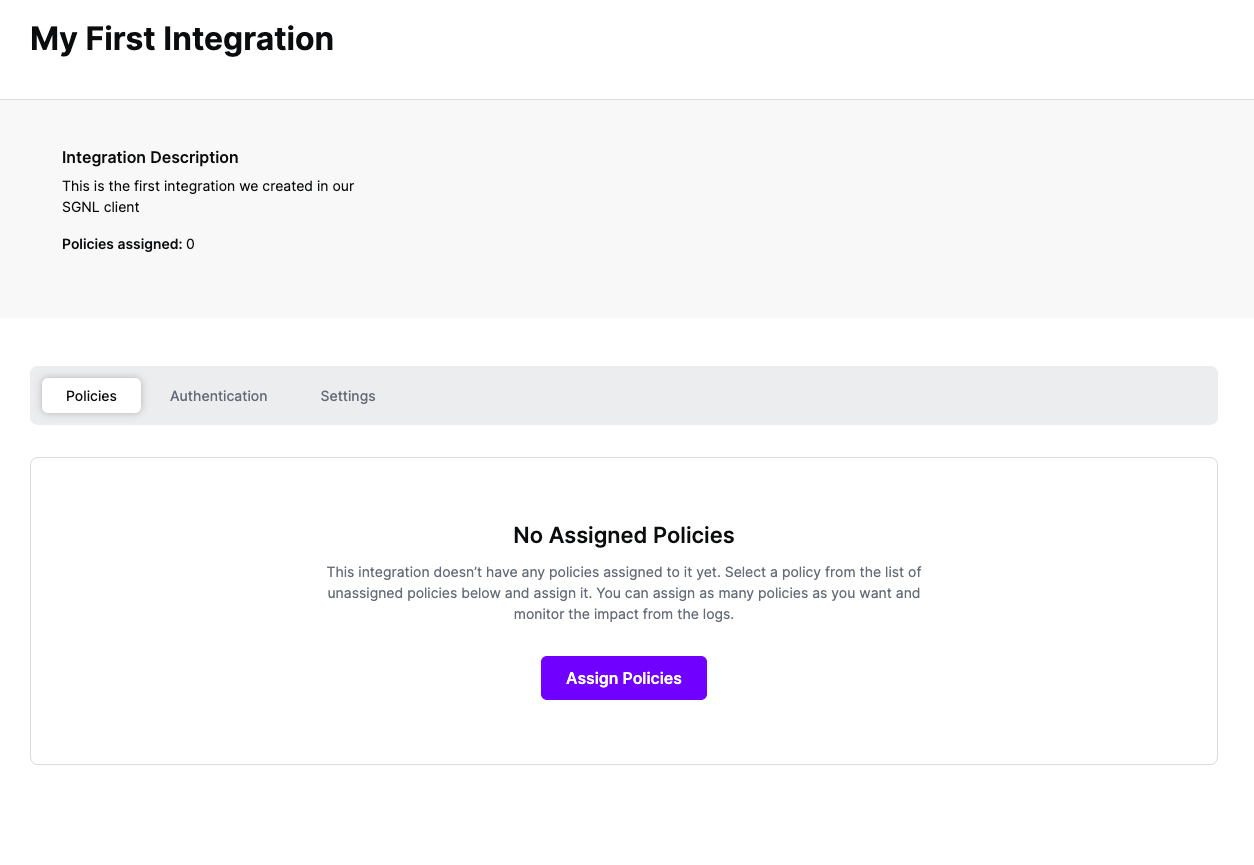
Select ‘Assign Policies’
Select:
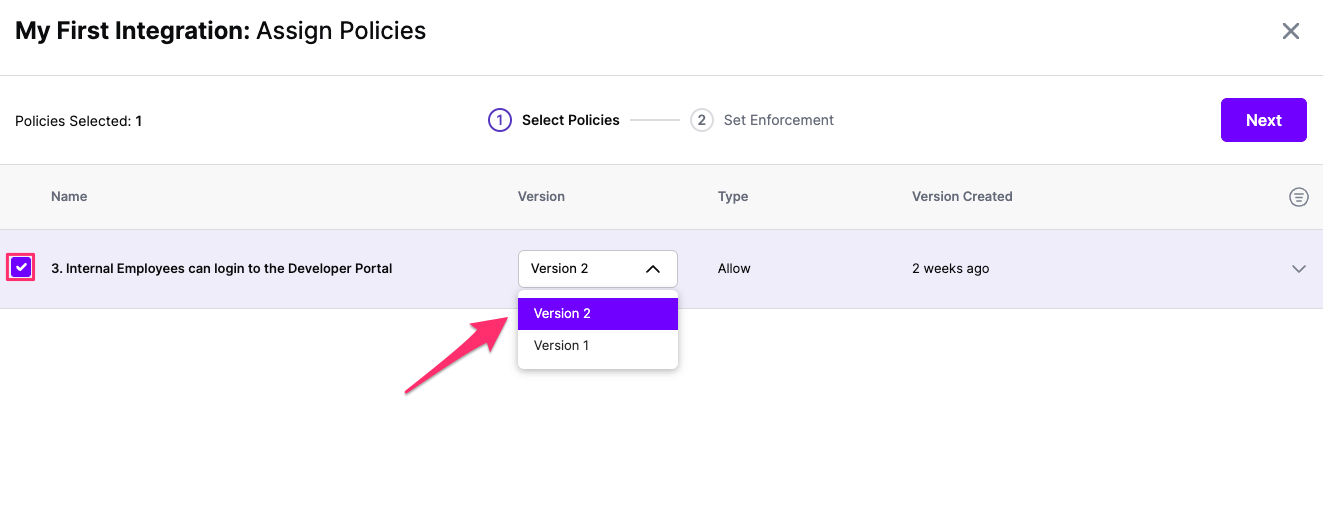
Click Next once you have the Policies and Versions configured as is appropriate
Select the Enforcement mode for the Policies you chose in the previous step
Simulated: Policy Versions that are being simulated will only log their access decision in the SGNL logs and will not impact the access decision that SGNL hands back to an integration. Simulated policies are useful for performing what-if analysis of new policy versions as well as debugging policy changes.
Note: It’s considered best practice to start with policies in Simulated mode, to verify that policies have been created an applied as expected
Enforced: Policy Versions that are being enforced will impact the access decisions that SGNL hands back to an integration. Enforced Policies will determine access for an integration
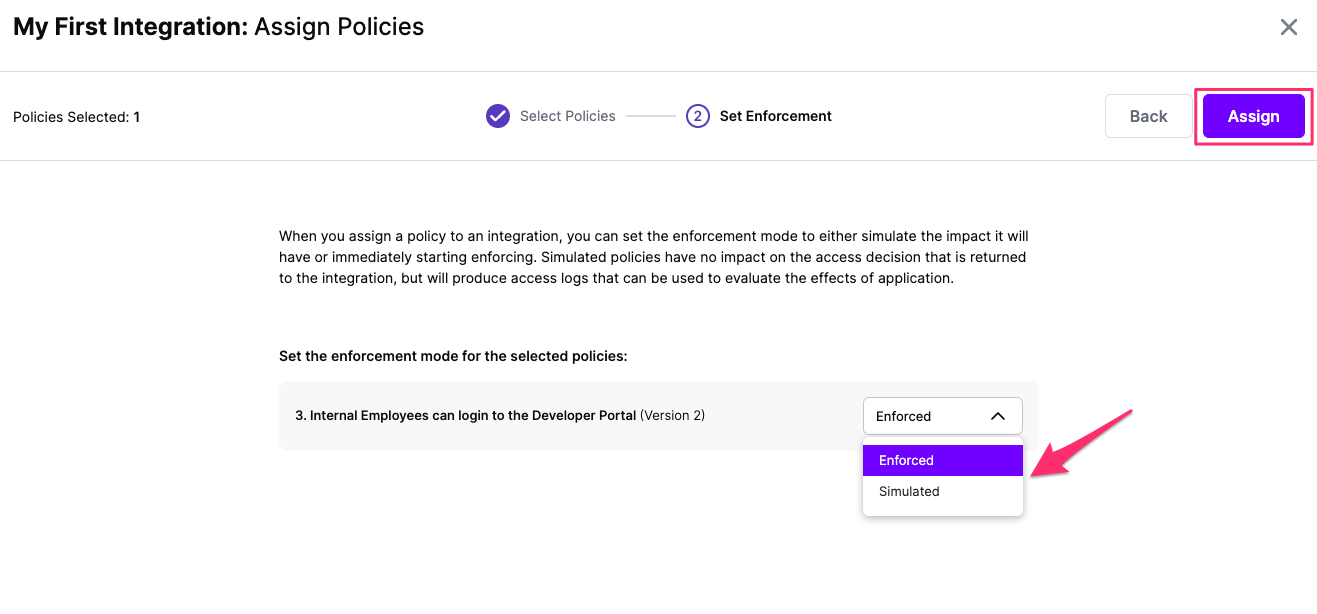
Select your desired Enforcement mode and select Assign
Versions of Policies will now be Assigned to your integration