Creating and Configuring an Okta System of Record
Prerequisites
- An Okta User account with elevated privileges to read the Okta APIs
Permissions Required
- Ability to add a new API Service Integration with scopes:
- okta.users.read, okta.groups.read
- Ability to generate an Okta API Key (if using an API Key method of authentication)
- Ability to read User and/or Group objects that are needed to be synchronized to SGNL
Configuring Okta
Using OAuth2 with an API Service Integration
- Login to your Okta Organization and select Applications from the left-navigation menu
- Choose API Service Integrations and select ‘Add Integration’
- Find and select SGNL in the list of integrations then choose ‘Next’
- On the ‘Authorize SGNL’ page, choose to ‘Install & Authorize’ SGNL
- On the next screen, you will have a single opportunity to copy your ‘client secret’ – copy it and keep it somewhere safe, you’ll need this to configure SGNL in a moment
- Once copied, select ‘Done’
- In the ‘General’ tab, copy the ‘Client ID’ - you’ll need those to configure SGNL in a moment
- By default, the new API Service integration will use scopes ‘okta.users.read’ and ‘okta.groups.read’ to support the synchronization of users and groups from Okta
- (Optional) Give the App an image to make it more easily discernable later
Using an API Key
- Login to your Okta Organization with the desired User Account that will be responsible for synchronization - note the Okta sub-domain you use to sign-in to this organization
- Note: SGNL and Okta recommends using an account that does not belong to any individual, but instead acts as a service account in Okta
- Create an Okta API Token
Configuring SGNL
Login to the SGNL Console
From the left menu, select Systems of Record
Click “Add System of Record” or “Add”.
The SGNL SoR Catalog will show up on the screen
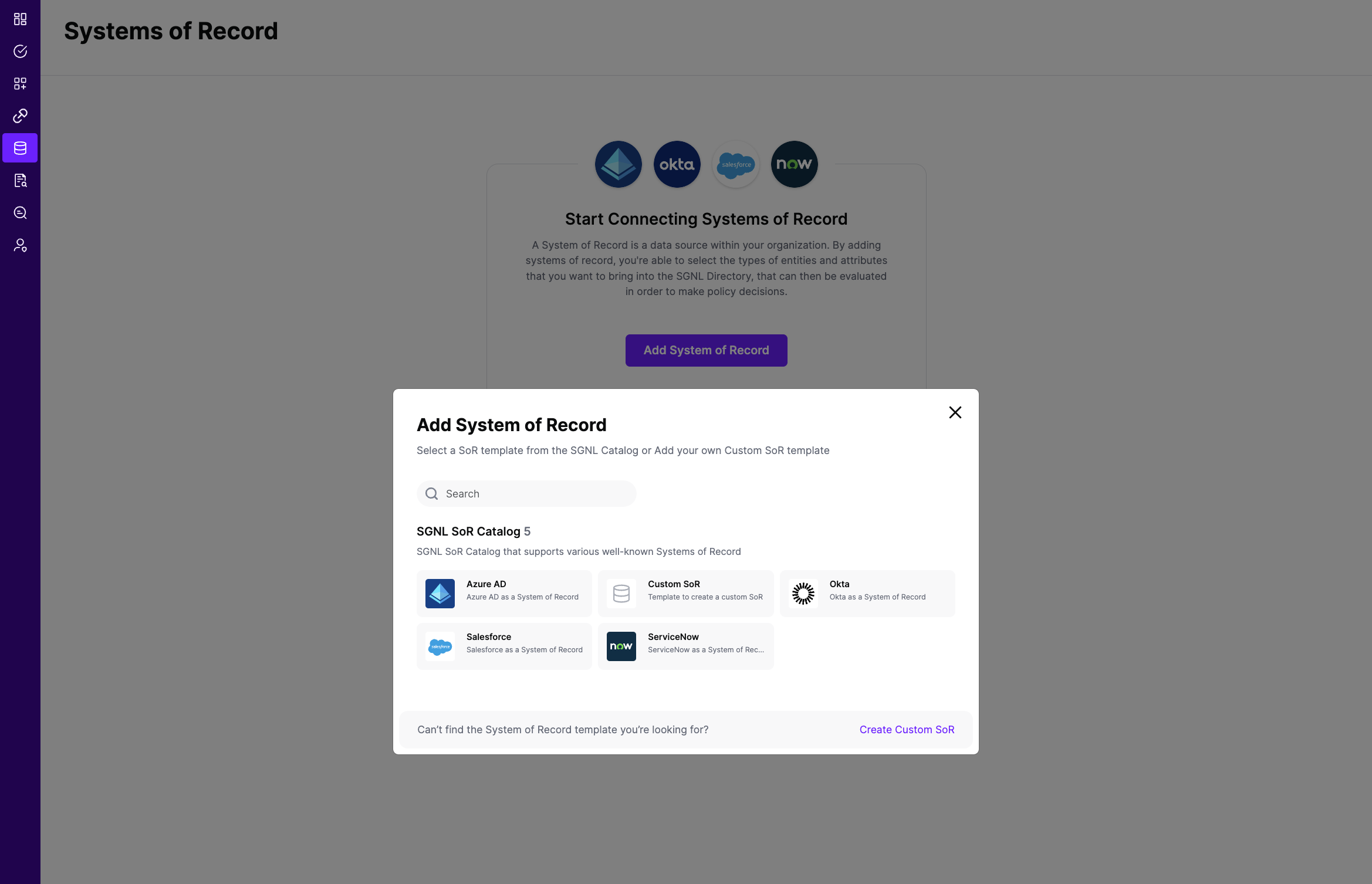
Click on “Okta” which will open up the New System of Record screen with some configuration options pre-populated from the Okta SoR template.
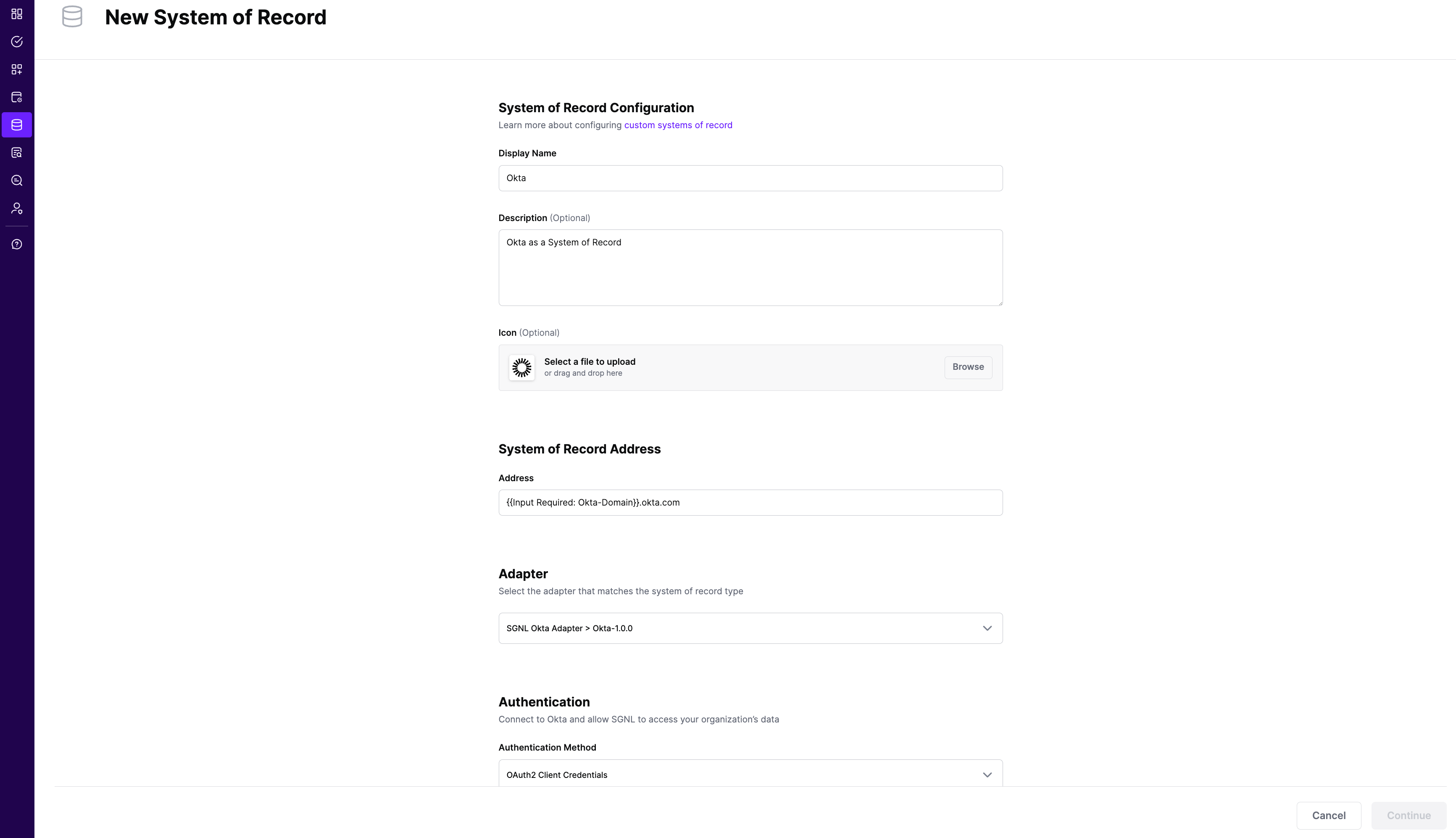
Choose the correct adapter that matches the Okta System of Record Type.
Select the Authentication Method - SGNL recommends using OAuth2 Authentication using an Okta API Service Integration
Replace all fields that have the {{Input Required:}} placeholder with relevant information. The following fields are required:
Okta Domain: Enter the domain you use to login to Okta. Generally, this takes the form of https://acmecorp.okta.com
If you are using OAuth2 authentication for the API Service Integration
- Client ID: Enter the Client ID you copied previously from Okta
- Client Secret: Enter the Client Secret you copied previously from Okta
- Token URL: Enter the Okta Domain you use to login
If you are using an API key, choose Bearer asthe Authentication Method, and enter:
- Auth Token: Enter the API Key you generated in Okta, prefixed with needed Okta Token type of “SSWS " - note trailing space
Click “Continue” to save your Okta System of Record. You will be taken to the Okta System of Record page.
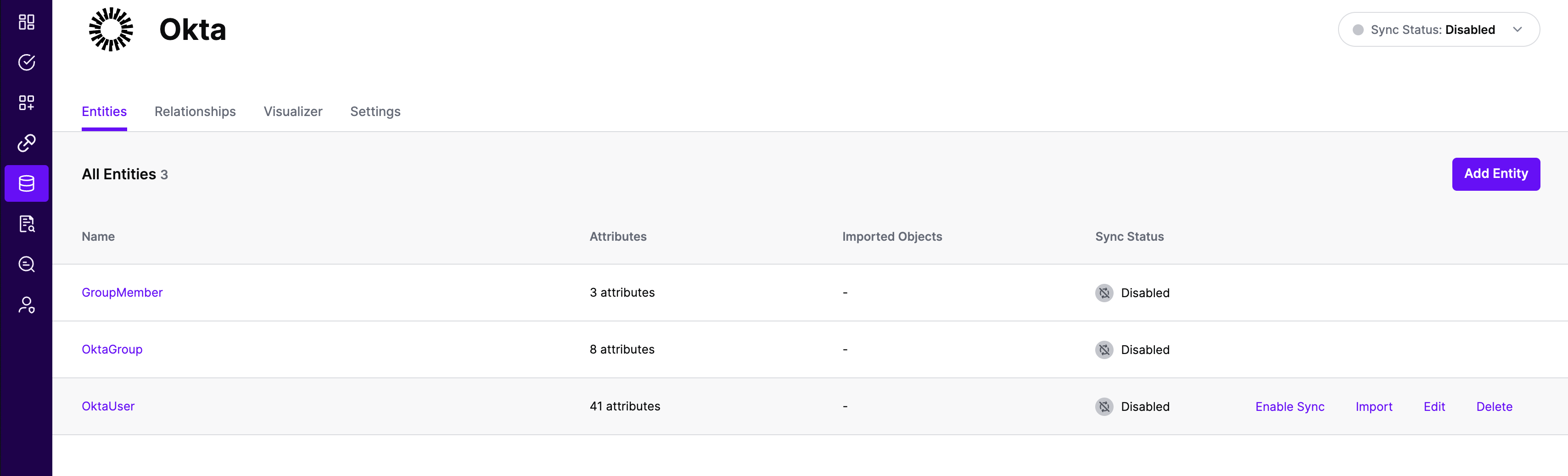
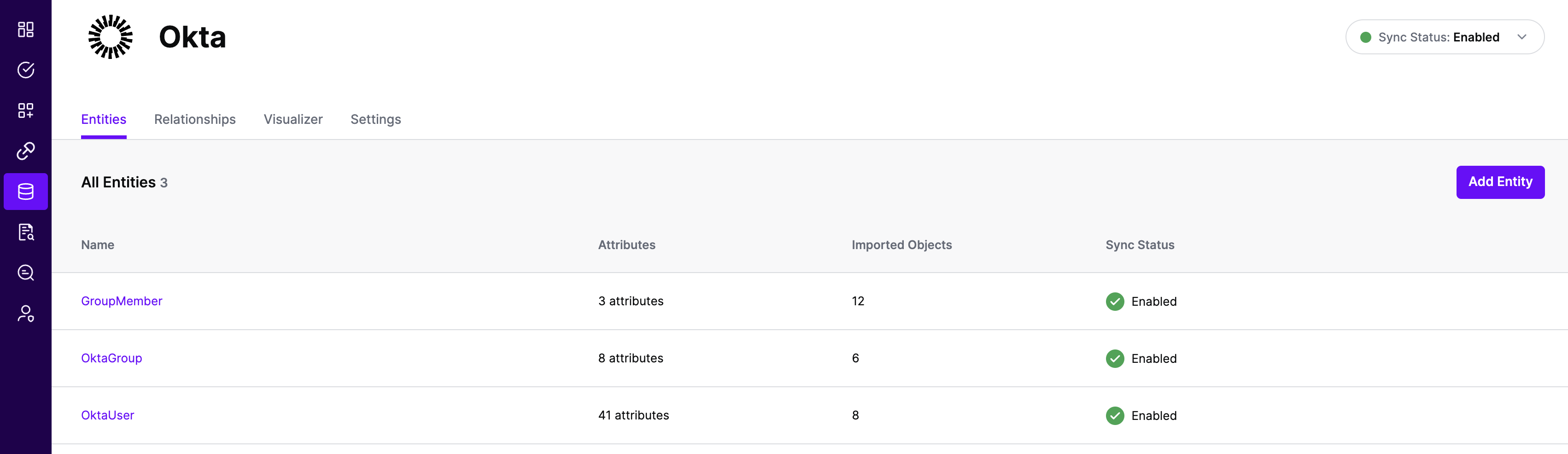
All entities and relationships are created as defined in the Okta template. If applicable, you can edit an entity and modify any properties of the entity or the associated attributes. Hover over the entity on the screen above to see the Edit button as shown above.
You can check the relationships created through the Relationships tab. However, relationships cannot be modified. You will need to delete an existing one, and create a new relationship.
(If applicable) You can also create relationships joining entities and attributes in Okta to entities and attributes in other Systems of Record configured in SGNL. For example, if User Employee Numbers in your ServiceNow instance are consistent with the User Employee Numbers in your HRIS system, you can create a relationship between the Employee Number attribute in the Okta instance and the Employee Number attribute in your HRIS System of Record. For more information on relationships, please refer to our Relationships page.
Note that synchronization is disabled by default when a new System of Record is created. You can choose to enable synchronization on Entities individually. Hover over the entity to see the Enable Sync button, and click on it.
Repeat for all Entities you want to synchronize to SGNL. Finally, Enable synchronization for the System of Record.
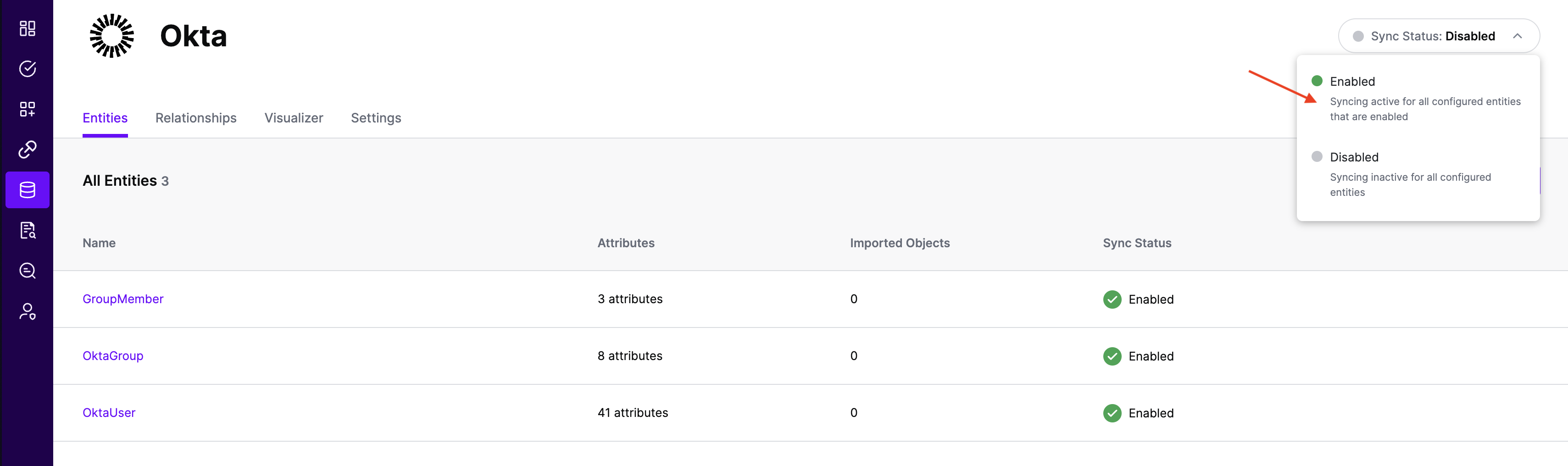
- After some time, SGNL should complete ingesting the data from your Okta instance into the SGNL graph. The number of objects ingested per entity are displayed on the Okta screen. You should then be able to construct policies based on your Okta data and make access evaluation calls to SGNL.
- Once ingestion is complete and Okta data is in the SGNL graph, you can use Data Lens to explore the SGNL graph.





